Entering 2024, the cybersecurity market is rapidly evolving, from cloud-native environments such as containers to the distributed workforce to the implementation of zero trust to the risks associated with generative AI (GenAI) and its rapid adoption and growth.
The surge in GenAI also means organizations must gain a full understanding of where data resides and how to manage access. Simultaneously, software and device supply chain attacks are intensifying, alongside a rise in regulatory demands. Balancing all these challenges becomes crucial to avoiding legal issues, meeting compliance requirements, and maintaining enduring customer trust.
In this environment, organizations must be equipped with the right tools to mitigate risks and ensure they aren’t caught flat-footed against a committed group of attackers, from nation-states to cybercrime groups, all looking to capitalize on poor security postures.
In this analysis, I’ll take a look at five of the most promising cybersecurity products and vendors to keep an eye on in 2024. All deliver innovative capabilities that customers can leverage in the constantly evolving battle against attackers.
CrowdStrike Falcon
The CrowdStrike Falcon XDR platform is a standout that recognizes the complexity of the modern enterprise. CrowdStrike boasts some of the most stable and impressive revenue growth ($786 million for the quarter ended last October, up 35% year over year) in the market among major companies, a testament to its adoption and trust from customers.
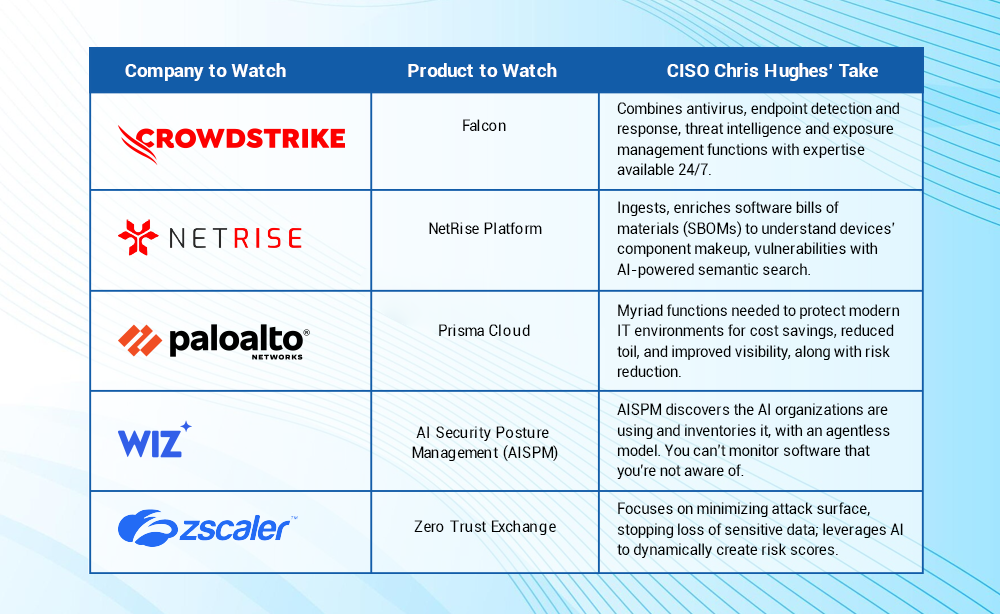
CrowdStrike Falcon combines multiple cybersecurity capabilities into a unified platform as opposed to requiring cybersecurity pros to manage multiple disparate products. It brings together critical features such as next-gen antivirus, endpoint detection and response, threat intelligence, and exposure management. Additionally, it provides managed detection and response (MDR) with 24/7 expertise on-hand, which is key as organizations struggle to attract and retain cybertalent.
The CrowdStrike Falcon platform, powered by AI, captures and monitors trillions of events per day, along with tracking several hundreds of known malicious actors. Another indicator of the company’s scale: Crowdstrike serves over 20,000 customers globally.
CrowdStrike Falcon also provides an asset graph, where cybersecurity pros can view managed and unmanaged devices in their enterprise, along with activities of devices, users, and workloads to make informed security operations decisions.
NetRise
A key trend in cybersecurity is the focus on supply chain security. One standout in this sector is NetRise, which has been focusing on firmware and Internet of Things (IoT) supply chain security, helping to identify and manage risks in firmware and software components of devices.
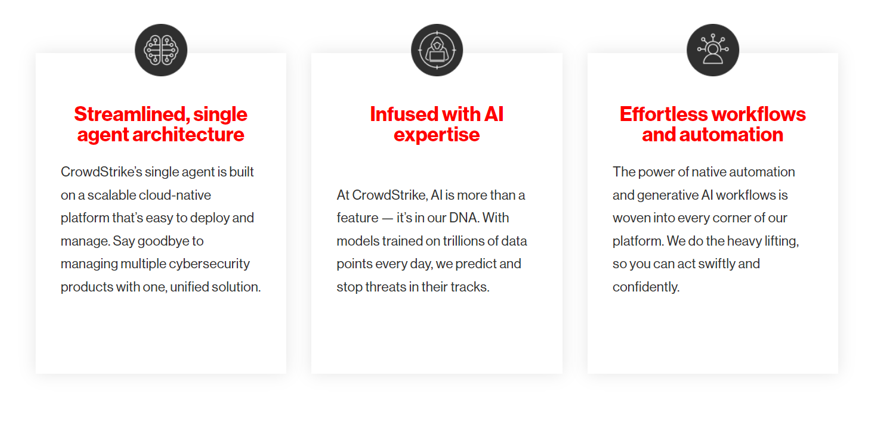
The NetRise platform offers tremendous capabilities including software bill of materials (SBOM) management, holistic risk visibility, continuous monitoring and compliance alignment. The platform allows users to generate, ingest, and enrich SBOMs to understand their device’s component makeup and any associated vulnerabilities.
Vulnerability management across an organization’s devices can be a daunting task, but NetRise allows for risk scores, using sources such as known vulnerabilities as well as the Cybersecurity and Infrastructure Security Agency’s (CISA’s) Known Exploited Vulnerability (KEV) catalog.
Ask Cloud Wars AI Agent about this analysis
It also offers the first of its kind AI-powered semantic search capability that lets users speak to NetRise Trace in natural language, looking for known vulnerabilities as well as potential attack paths and weaknesses, all of which can be displayed in a graph format for easier assessment and remediation.
Additionally, with increased calls and requirements for product security and supply chain compliance requirements, NetRise helps meet consumer and customer demands for device and software manufacturers. This includes providing transparency on the components of products, clear and comprehensive vulnerability disclosure and guidance for customers, and the ability to provide artifacts such as SBOMs and software build attestations.
The platform helps users meet a myriad of compliance requirements, such as those from the National Institute of Standards and Technology (NIST), Food and Drug Administration (FDA), Health Insurance Portability and Accountability Act (HIPAA), and more.
Palo Alto Networks’ Prisma Cloud
No current discussion of leading cybersecurity companies and products would be complete without mentioning Palo Alto Networks, whose Prisma Cloud platform continues to be an industry giant. Due to strategic acquisitions as well as key investments and innovations, Prisma Cloud provides a robust set of capabilities to help protect today’s dynamic cloud environments.
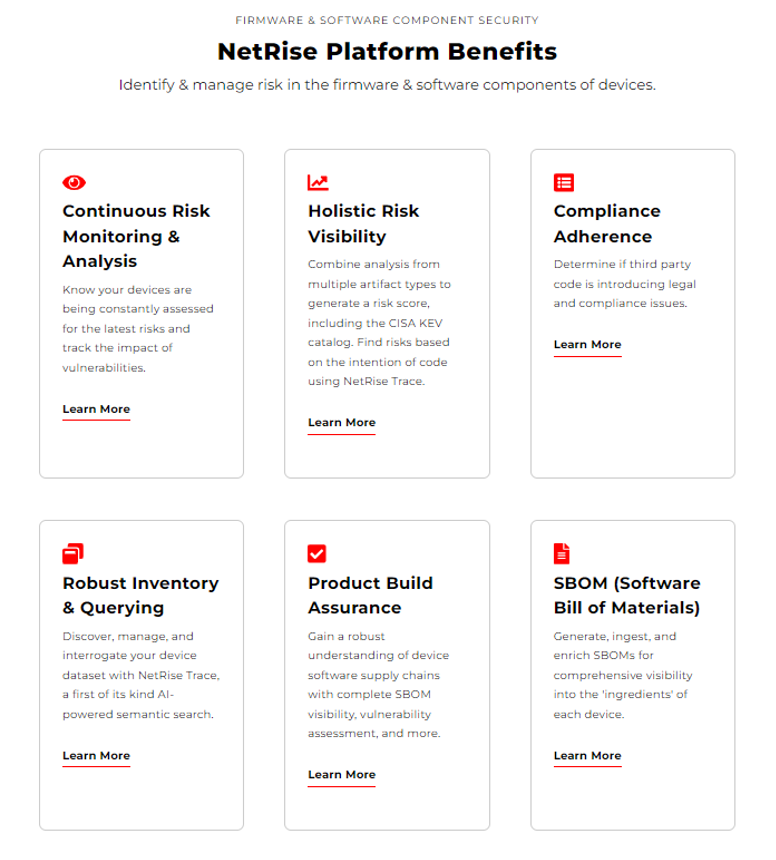
Some of its features include Infrastructure-as-Code (IaC) security, secrets scanning, continuous integration/continuous deployment (CI/CD) security, and software composition analysis. Additionally, the platform supports cloud security posture management (CSPM), entitlement management, agentless scanning, and exposure management. The real question becomes what can’t it do?
In the modern cybersecurity market, organizations generally find themselves using tens of security tools, often as independent point solutions, and then struggle to tie it all together or manage the hodgepodge of tools they have in their portfolio. This often leaves defenders stressed and experiencing cognitive overload as they try to make use of, and monitor, all the tools.
Palo Alto Networks brings together the myriad of tools and capabilities needed to protect modern IT environments into a comprehensive platform that can lead to cost savings, reduced toil and frustration and, ultimately, improved visibility and risk reduction.
Wiz AI Security Posture Management (AISPM)
Cloud-native security company Wiz’s AI Security Posture Management capability is part of the Wiz Cloud Native Application Protection Platform (CNAPP). CNAPPs are used for security and compliance in dynamic cloud environments to protect everything from endpoints to data and applications combining various capabilities including posture management and data protection.
Wiz recently announced its AI Security Posture Management (AI-SPM), claiming to be the first CNAPP to provide this unique capability. With organizations rushing to adopt AI tools, such as GenAI platforms including ChatGPT and countless others, they need a way to protect themselves from the associated risks.
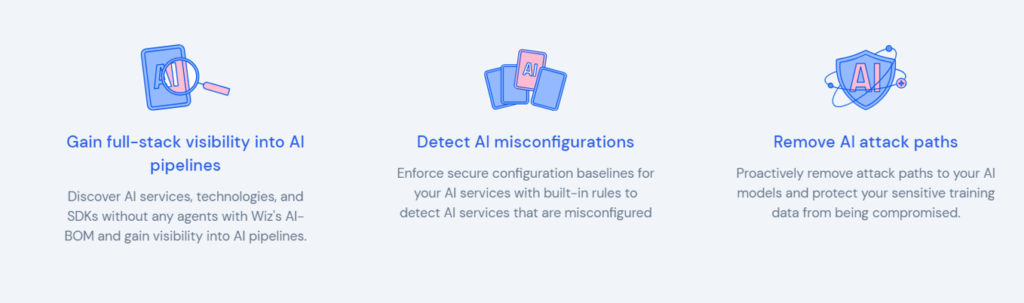
Wiz’s AISPM provides core capabilities including helping to discover and inventory the AI that organizations are using with an agentless architecture. This is key, given that you can’t protect what you don’t know exists. It also helps enforce AI configuration baselines, with the built-in ability to look for misconfigurations that can expose sensitive data or introduce risk.
Wiz also provides data security posture management, allowing organizations to control what data goes into AI services and tools and enforce configuration checks as discussed above to ensure sensitive data is properly safeguarded.
Last but not least, Wiz AISPM allows attack path analysis, helping visualize potential attack paths and presenting findings from all of the features discussed above in a comprehensive AI security dashboard for security practitioners and leaders alike.
Zscaler Zero Trust Exchange
There’s no denying that we increasingly work in a distributed environment, with users often working remotely from home or wherever they like. This fact, coupled with the adoption of bring your own device (BYOD) practices, creates real challenges for the modern enterprise compared to legacy on-premise, in-office approaches to cybersecurity.
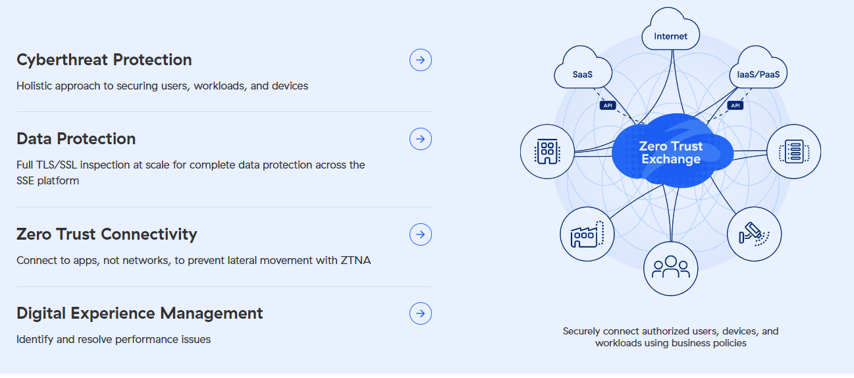
Employees and contractors are accessing systems, including sensitive data and proprietary business applications and systems, from all over the world. Zscaler’s Zero Trust Exchange helps address this challenge head-on, incorporating key aspects of the zero trust methodology in its comprehensive platform.
Its platform focuses on key activities such as minimizing the attack surface, preventing compromise, eliminating lateral movement, and stopping the loss of sensitive data. It is all built on the concept of no implicit trust, meaning no user, workload, or device is automatically trusted; they must be verified and have relevant protections and controls applied to mitigate risk.
This all occurs regardless of where a user or device is connecting from: the Internet, Software as a Service (SaaS) or cloud environments or on-premise data centers and associated systems.
Zscaler’s Zero Trust Exchange platform allows for the encryption and decryption of data, deep packet inspection, and the use of dynamic access control to generate policies, on the fly, that align with the organization’s risk tolerance and the unique connectivity scenario at hand. It also leverages AI to dynamically create a risk score of the requested access using context such as the device’s posture, threats, intended connectivity destination, and organizational policy.
More Analysis on Top Products for 2024: