An exploration of the NSA’s software supply chain security guidance and how it can help organizations fortify overall cybersecurity.
Vulnerability management
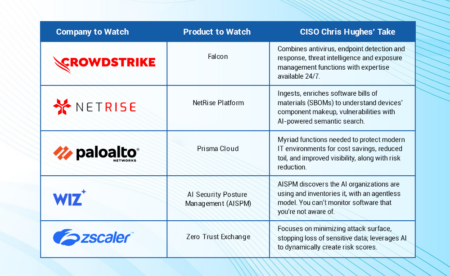
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
Discover the hidden risks embedded in AI code, including false security assumptions and a pattern of bypassing policies.
OWASP has updated CycloneDX to support machine learning models, as the next generation of AI continues to enhance technology.
Employment identity theft is a growing concern for individuals and businesses. Learn how to protect yourself and your organization from becoming a victim.
An in-depth look at automated vulnerability scanning within financial software, how it works, as well as top tools and best practices to get the job done.
Endor Labs released a report that identifies the top 10 open source software risks, including known vulnerabilities, compromised legitimate packages, untracked dependencies, and more. Chis Hughes explains.
AI and automation can protect against financial and reputational losses from data theft and ransomware in financial software, writes Bill Doerrfeld.
The rise of software-as-a-service presents new business opportunities, but also new security challenges that need to be balanced with business enablement to ensure growth and protection. This guidebook on Securing Software-as-a-Service Applications, underwritten by Lookout, provides expert insights on how to integrate SaaS securely into businesses.
Nearly all cloud security incidents are due to customer misconfigurations. Chris Hughes explains how cybersecurity hygiene addresses the problem.
Contextual analysis makes Application Security (AppSec) more efficient by identifying the most exploitable vulnerabilities, CISO Chris Hughes says.
Digital transformation has brought on a new level of cybersecurity concerns around applications, and those need and those concerns warrant CEO focus, Tony Uphoff says.
The capabilities of Snyk for automatic discovery & remediation have positioned it to shift security left. However, vendor solutions only go so far.
After a breach, you’ll want to stop data loss as soon as possible, but it comes with risks and other drawbacks. Frank shares tips to arm you with the knowledge, options, and flexibility to advise your business on the right approach.
Burned out security and software teams are hard to retain and increase the odds of a breach. Bill speaks with Object First’s David Bennett, about how he tackles the issue as an object storage solution startup CEO.
In episode 32, Chris looks at a new Cybersecurity Infrastructure Security Agency post that focuses on three critical steps for advancing vulnerability management across the ecosystem in IT.
Analyst Chrus Hughes takes a look at EPSS, a new approach to evaluating vulnerability that takes into account not only criticality and scores, but also exploitability.
Chris provides takeaways from the Cyber Safety Review Board’s recent Log4j incident report.
Cybersecurity has evolved beyond the “office of ‘no'” to a true business enabler that requires an on-going vigilant effort to keep a resilient security posture
What’s in a vulnerability score? Chris Hughes explains what these are, where they come from, and how cybersecurity professionals should approach them.