The Model Context Protocol (MCP) has been hailed as a powerful step forward in AI agent interoperability, providing a clear specification for agents to access data and resources stored on external systems — thereby providing the requisite context to capitalize on the power of AI.
As such, it has been embraced by AI experts, customers, and vendors as the industry strives to build the underlying infrastructure and communications capabilities to fully unlock agentic AI in the multi-vendor software stacks that are so prevalent in corporate America.
At the same time, security experts raise concerns about the need to protect data as agents work together and are beginning to issue guidelines on how to go about securing MCP.
One noteworthy example of tracking vulnerabilities and providing real-time guidelines on how best to protect — and capitalize on — MCP is the Vulnerable MCP Project, which serves as an invaluable resource for agentic AI users, developers, partners, and vendors.
In describing its mission, the project notes that MCP “enables AI systems to access tools and external resources, but this capability introduces new security challenges. By documenting these vulnerabilities, we aim to promote safer implementation practices and contribute to the overall security of AI systems.”
CISO and Security expert Chris Hughes called the Vulnerable MCP Project an “awesome resource” in a LinkedIn post: “MCP is poised to facilitate the rise of agentic AI architectures and autonomous workflows among agents. That said, it also comes with potential pitfalls, including an expanded attack surface, exploitation, lateral movement, and authorization gaps.”
MCP Background
The infographic below provides a clear, concise explanation of how MCP operates, providing data access in a client/server architecture:
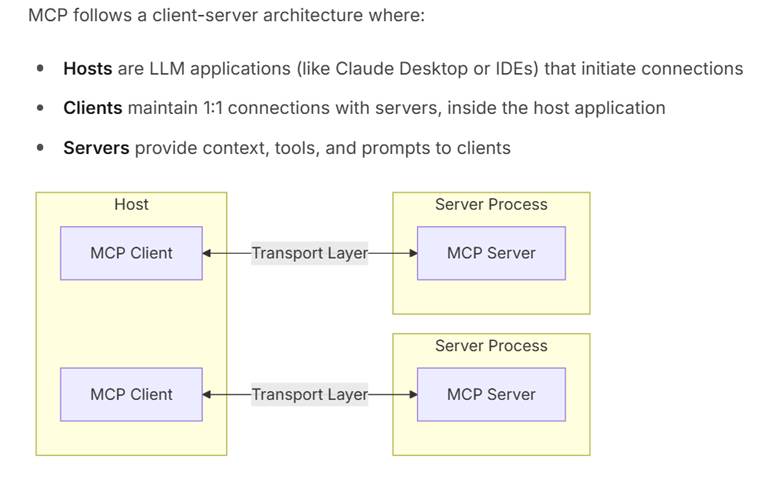
Source: https://modelcontextprotocol.io/docs/concepts/architecture
Before diving into security issues, I’ll cover one point that’s critical to understand in any discussion regarding MCP, which is that MCP is not competing with the Agent2Agent protocol promulgated by Google — indeed many of the key vendors backing A2A also support MCP.
A2A handles task coordination between agents, supporting long-running, complex workflows that require those agents to work together. While A2A provides built-in authentication and authorization features for security, MCP requires additional configuration for secure access to data.
Vulnerable MCP Project Resources
As a community resource, the Vulnerable MCP Project actively seeks community input on vulnerabilities that have been discovered. As of today, the latest report is on tool function parameter abuse, which is classified as “high” and explained as follows:
“Malicious MCP servers can extract sensitive information by abusing tool function parameters. Information such as chain-of-thought, conversation history, previous tool call results, and full system prompt can be extracted by inserting parameters such as ‘system_prompt’ or ‘conversation_history’. This attack technique can be used to exfiltrate sensitive information from user input or model response, understand what other tools the user has at their disposal that can be taken advantage of, as well as find ways to abuse the model itself.”
More broadly, the project’s website notes the following security implications that come with MCP usage:
- MCP provides AI systems direct interaction with external tools and data
- If compromised, consequences include data leaks, unauthorized AI actions, and potential real-world harm
- Securing MCP is essential for trustworthy AI systems in complex enterprise environments
It also specifically identifies six enterprise-critical threats that can play out when required security controls are lacking:
- Tool poisoning, or the malicious manipulation to induce unintended or harmful actions by an AI model
- Exfiltration of sensitive data through compromised tools or manipulated MCP responses
- Establishment of command and control channels via compromised MCP servers or tools
- Identity and access control subversion to gain unauthorized access or increase privileges
- Insertion of backdoors or malware through compromised MCP server or tool update channels
- Denial of service by overloading MCP servers or dependent resources

AI Agent & Copilot Summit is an AI-first event to define opportunities, impact, and outcomes with Microsoft Copilot and agents. Building on its 2025 success, the 2026 event takes place March 17-19 in San Diego. Get more details.
Security Frameworks and Checklists
Other resources that make this project so valuable include its proposed seven-layer security framework and security checklists that tech and IT pros can utilize to lock down their MCP usage. The seven layer framework covers:
- Network Layer
- Application Gateway Layer
- Container/Host Layer
- Identity & Access Layer
- Tool & Prompt Management Layer
- Input/Output Validation Layer
- Operational Security Layer
It also delivers an exhaustive list of security mitigations to protect MCP servers and clients.
The project includes a highly detailed security implementation checklist — another invaluable resource for those considering or implementing MCP. This includes:
Foundation security that calls for robust input validation, clear context boundaries, output filtering, least privilege principles, comprehensive logging, regular security testing, and maintaining updated dependencies.
Advanced protection that includes sandboxes for MCP servers, cryptographic verification of tool definitions, behavior-based monitoring for anomaly detection, machine-learning based detection for sophisticated attacks, a centralized tool registry, network segmentation for MCP isolation, and just-in-time access for sensitive operations.
Enterprise considerations including integration with the existing security architecture, single sign-on and multifactor authentication, adding MCP expertise to the Security Operations Center, compliance monitoring, secure MCP development lifecycle, regular security training for developers and users, and supply chain security for MCP components.
Closing Thoughts
The Vulnerable MCP Project makes clear that capitalizing on the benefits of MCP is possible, but not without considerable security planning, governance and execution. That is, at least in part, because the MCP specification didn’t inherently account for enterprise security considerations.
“Because you have agents communicating with each other, all of a sudden the blast radius becomes wider, so one agent compromised can compromise another agent,” said Michael Bargury, CTO and co-founder the agentic AI security firm Zenity.
“There are so many things that can be improved on these protocols (MCP and A2A) right now, but they are pretty young protocols, and what I see both from A2A and MCP is they’re listening to the feedback and working together with the cybersecurity community to make the protocols themselves more robust, and have more security built in,” Bargury added.
Add the Vulnerable MCP Project as one important contribution to the community’s effort to unlock the full power and potential of MCP. As Bargury noted: “The bigger picture is that MCP and A2A are wonderful protocols that allow agents to be more productive.”
Ask Cloud Wars AI Agent about this analysis