
As companies continue to ramp up their cloud investments (overall cloud spending is expected to increase 21% to $724 billion in 2024), they are leaning further into cloud service providers (CSPs) to offload traditional infrastructure operations so their in-house tech teams can focus on their core competencies including business applications and corporate data.
As this shift plays out, cloud infrastructure is growing increasingly complex: Companies are deploying hybrid and multi-cloud architectures as well as serverless architectures that tap into Kubernetes, containerization, and microservices.
Traditional “detection and response” cybersecurity platforms face stark challenges in navigating this complexity while conducting effective risk mitigation.
In this Innovation Profile, I’ll explain through my chief information security officer (CISO) lens how Wiz’s cloud-native application protection platform (CNAPP) offers security practitioners and organizations the comprehensive tooling they need to conduct effective cloud detection and response (CDR).
Ask Cloud Wars AI Agent about this analysis
New Paradigm: Detection and Response in the Cloud
While traditional security metrics such as mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) are still relevant in the cloud, their value is reduced by the dynamic, ephemeral nature of cloud computing infrastructure and applications. Furthermore, cloud computing has ushered in a paradigm shift whereby developers are often taking ownership of the infrastructure they run their applications on.
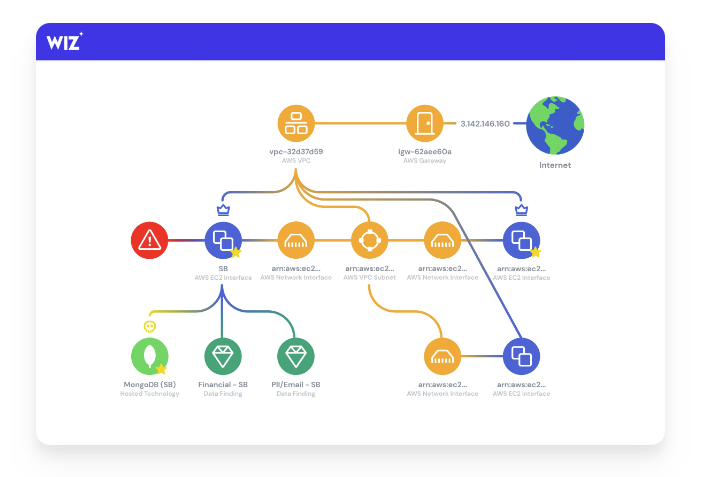
These developments underscore the need to continuously monitor workloads, gather intelligence from the CSPs, and quickly respond to threats. In the organizations I work with, I find that most teams struggle to develop cloud-native incident response playbooks and facilitate their execution from evidence gathering to ensuring containment through to recovery.
The Wiz platform supports these detection and response activities through out-of-the-box incident response (IR) playbooks and leveraging cloud-native services to facilitate automated IR execution. This minimizes the exploitation window that’s available to malicious actors while hindering their ability to move laterally within a company’s tech environment or compromise sensitive data.
Navigating Cloud Layers
You may have heard of the four Cs of cloud-native security: Cloud, Cluster, Container, and Code. The four Cs must be actively managed to properly secure cloud-native environments; doing so will ensure security throughout the entire software development lifecycle (SDLC), from development to runtime.
To deliver on the four Cs, organizations need to not only identify malicious activity and vulnerabilities in a single layer of the cloud-native paradigm; they must actually piece together context across those layers (CSP events and runtime events) of modern digital environments to distinguish benign from malicious activity, thereby helping to maximize use of limited resources and eliminate false positives.
Those of us who work in cybersecurity every day know that not all vulnerabilities and assets are the same when it comes to criticality and risk. To address this point, Wiz supports context-driven risk prioritization based on an asset’s or dataset’s criticality to the organization, coupled with enriched vulnerability and threat data across the layers of cloud-native environments.

This doesn’t mean customers should expect a cumbersome data dump with a massive list of findings; instead, the Wiz platform provides dashboards and visualizations that can demonstrate potential attack paths and considerations for the remediation process.
Wiz’s Cloud Detection & Response performs behavioral detection across various layers from code to the cloud environment, including runtime telemetry and analysis. Plus, practitioners know that not all vulnerabilities are equal; key considerations such as known exploitation, exploitation probability, reachability, and the criticality of the vulnerable asset all must be accounted for to help defenders properly prioritize their remediation efforts and maximize their use of limited resources, including time.
Furthermore, Wiz provides attack path visualizations, leaning into the line “defenders think in lists, attackers think in graphs.” Being able to visualize not just vulnerable assets but the interrelated nature of the assets across the enterprise and the potential attack paths that can be exploited enables defenders to think like attackers and acts as a force multiplier in communicating risk to executive leadership and engineering peers as well.
Using CNAPP to Power Cloud Detection and Response
Ongoing market analyses — as well as direct experience — indicate that security practitioners and teams experience cognitive overload from managing dozens of disparate security tools. This typically includes a combination of open source and proprietary tooling, which tend to be neither technically integrated nor able to leverage context from other tools.
The Wiz CNAPP unifies and tightly integrates a set of security and compliance capabilities to protect cloud-native applications throughout the SDLC. This helps address common challenges including:
- Siloed security tooling
- Lack of comprehensive security context
- Gaps that exist between developers — who are writing code and deploying systems — and security teams monitoring those environments and systems for vulnerabilities, risks and malicious behavior
While several vendors have built CNAPPs, many have taken the path of acquiring startups and products that then need to be integrated and stitched into their platform. While this approach can work, it isn’t seamless and can have challenges, such as a disjointed user experience, and struggles with data integrations across products that can become technical debt when not properly prioritized. The organic development approach, by contrast, leads to frictionless user experiences and optimized risk mitigation, rather than a technical kludge that impedes secure outcomes.
Cross-Team Empowerment
Development and cybersecurity teams have an increasing focus on creating and enforcing security earlier in the development lifecycle (commonly referred to as shifting security left) and breaking down silos while embracing DevSecOps. When successfully achieved, these objectives lead to cross-team empowerment.
Empowerment in this context means those closest to the code and infrastructure — often developers — clearly understand, and can aid in, risk reduction. Wiz’s CNAPP allows security teams to provide visibility to their engineering and development peers to leverage their direct infrastructure and application context to best mitigate cloud-native risks. It also helps aid security operations center (SOC) and IR professionals by being able to visualize attack paths with context-rich vulnerability data, aiding in detection and response challenges in the cloud that legacy tools struggle with.
Why Wiz Belongs on CISOs’ Shortlists
The proliferation of cloud computing, hybrid cloud architectures, and serverless, combined with shifting tech organizational dynamics, necessitates a new paradigm in cloud-native security.
While traditional tools built for detection and response are able to add some value, cloud-native architectures offer the most robust platforms to secure cloud-native environments and facilitate collaboration between the expanding range of stakeholders working on a company’s cloud infrastructure. Wiz warrants close evaluation by CISOs in this context.










