Threat intelligence serves as a key capability within robust cybersecurity programs, utilizing data to help security leaders be proactive about the investments, technology, and other measures they take to mitigate risk to the organization.
For those who are unfamiliar with the term, threat intelligence is defined by cloud security company Crowdstrike as “data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors.” In other words, it’s research to determine how and why your organization might be vulnerable to cyber-attacks.
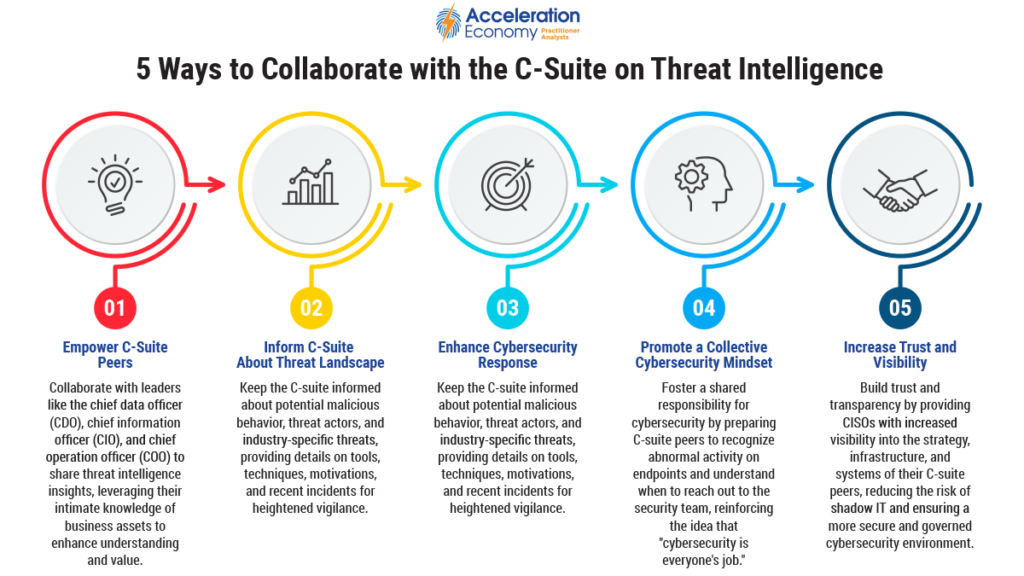
There’s an important organizational consideration when it comes to the use of threat intelligence. Success requires coordinating with other C-suite executives to ensure the value of threat intelligence, understand threat actors, and manage organizational risk.

Which companies are the most important vendors in cybersecurity? Check out
the Acceleration Economy Cybersecurity
Top 10 Shortlist.
How to Collaborate With Other C-Suite Members
Sharing insights from threat intelligence with your fellow C-suite members can be a force multiplier. Think about it: Threat actors aren’t generally targeting the CISO, or security, but instead the organization’s data, systems, and business operations. These business assets belong to your C-suite peers such as the chief data officer (CDO), chief information officer (CIO), and chief operating officer (COO), to name a few. These leaders have more intimate knowledge of the business, its data, and its operations than the CISO, so collaboration with them is critical, and it will go a long way toward helping them understand the value of threat intelligence.
Taking insights from threat intelligence and sharing them with your C-suite peers helps keep them informed about potentially malicious behavior that the organization may experience, as well as about threat actors and behavior that competitors in your industry are facing. This means informing them regarding malicious actors’ tools, techniques, and behaviors as well as motivations and recently reported incidents that can keep them vigilant as they perform daily activities that could make their business processes a target of malicious actors.
Why Sharing Threat Intelligence Works
By engaging your C-suite peers, you will empower them to understand the threat actors’ tactics, techniques, and procedures (TTPs), positioning them (and their staff by extension), to be better equipped to identify and respond to malicious or suspicious behavior. It is often said that “cybersecurity is everyone’s job.”
If we’re going to embrace this mindset, then we need to prepare people accordingly. This means helping C-suite peers understand what activity on their endpoint may be abnormal, or what sort of communications, such as phishing text messages, should warrant reaching out to you and your security team.
This type of engagement increases trust and transparency, and it lets the CISO get more visibility into the strategy, infrastructure, and systems of their C-suite peers. It also provides more context on how systems are being used, with what sort of data, and for what purposes. Lack of visibility leads to shadow IT, which is ungoverned by cybersecurity and often results in unaddressed vulnerabilities and risks.
The business ultimately owns the risk and generally makes decisions about what risks to address or accept. As such, engaging the organization’s primary decision-makers with threat intelligence positions them to have a clear understanding of the risks and threats facing their organization and ultimately enables them to make decisions and take actions based on data.
Final Thoughts
We increasingly see efforts to break down silos in support of cybersecurity objectives. This includes approaches such as DevSecOps, which is a high priority in the federal sector where I spend a lot of my time, and in the practice of leveraging cybersecurity as a business enabler. This cross-disciplinary collaboration (and silo-breaking) takes place as a result of intentional engagement, outreach, and education by the CISO and security staff. Threat intelligence is a valuable asset to ensure you’re leading the drive to higher engagement.
This article has been updated since it was originally published on April 25, 2023.











