Gain CISO insight into Databricks’ AI security framework with an expert review that includes crucial strategies for safeguarding AI models without impeding business innovation.
New data clean room app — integrated into the Snowflake Data Cloud — makes cross-company, cross-cloud data sharing secure and easily accessible.
Databricks’ AI Security Framework illuminates the path to secure and compliant AI adoption, addressing critical security risks across various stages of AI systems.
Leveraging Google’s cybersecurity intelligence, Google Cloud emerges as a formidable player, poised to capitalize on market opportunities amid competitive challenges.
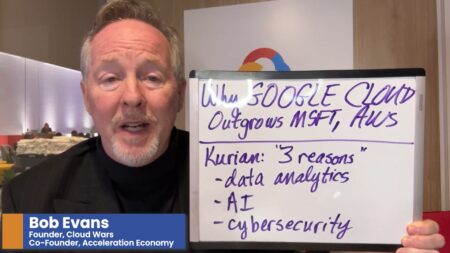
During Google Cloud Next, CEO Thomas Kurian cites three reasons why Google Cloud is growing faster than its competitors: data analytics, AI, and cybersecurity.
AI Ecosystem Report Ep 34: NVIDIA and Hippocratic AI partner to develop AI healthcare agents; BigID secures funds for its AI-powered data security offerings; and Elon Musk launches Grok, a real-time chatbot for the X platform.
Microsoft faces scrutiny over a cybersecurity intrusion in China, prompting questions about how CEO Satya Nadella will address the crisis to regain customer trust.
AI, spearheaded by CrowdStrike and Google, is redefining cybersecurity, shifting it from a risk to an indispensable asset, revolutionizing defense strategies against evolving threats.
This report highlights IBM innovations that result in the Cloud Wars Top 10 company being listed on 5 out 8 categories for products to watch in 2024 by our practitioner analysts.
Mastering soft skills transforms cybersecurity professionals into strategic communicators, empathetic collaborators, and compelling storytellers.
There’s been a surge in sophisticated phishing techniques, outlined in Lookout’s research, targeting cryptocurrency platforms and federal agencies like the FCC.
With a $2M commitment, Google spearheads the AI Cyber Defense Initiative, sharing the Magika AI tool, and uniting with global startups, marking a significant move towards strengthening cybersecurity resilience.
Gutsy redefines cybersecurity with process mining, a strategic tool that integrates people, processes, and technology to offer data-driven insights.
AI Index Ep 28: Super Bowl commercials highlight generative AI; Perplexity raised $73.6M; and Pecan AI develops predictive-model offerings.
Nation-states, including China, Iran, North Korea, and Russia, are reported to be utilizing AI, particularly OpenAI’s platform, for malicious cyber activities.
Analyzing the role of AI in manufacturing, this CIO guide explores efficiency gains, quality control improvements, and predictive maintenance benefits, while addressing cybersecurity, data privacy, and technology dependency risks.
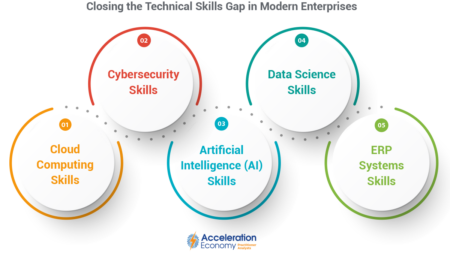
In order to prepare companies for the future of technology-driven business, it’s incumbent upon CIOs to identify and actively address the most critical tech skills gaps.
IBM research gives CEOs advice on how to ensure people and skills adapt to GenAI, top use cases to consider, and where they can get the most bang for the buck.
HYCU uses low code/no code and generative AI to simplify integrations for data protection of SaaS applications.
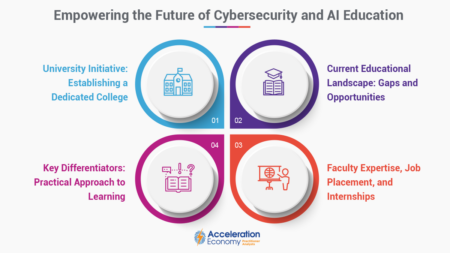
Texas university leads the charge in cybersecurity education, introducing a specialized college focused on AI and cybersecurity. Students need academic and real-world experience to succeed in these domains.