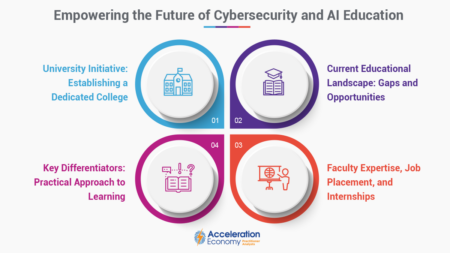
Texas university leads the charge in cybersecurity education, introducing a specialized college focused on AI and cybersecurity. Students need academic and real-world experience to succeed in these domains.
AI Index Report Ep 26: ASU embraces OpenAI’s ChatGPT Enterprise; Blueshift gains $40 million in growth investment; and Vicarius builds cybersecurity copilot.
Thomas Kurian discusses how Google Cloud supports its customers, the application of AI, and its Gemini offering in this exclusive CEO Outlook 2024 discussion.
HYCU applies generative AI to a critical enteprise use case: easily, rapidly building code that enables companies to protect data stored in their SaaS applications.
This guidebook offers insights on making zero trust a reality in our businesses, minimizing vulnerabilities that come with SaaS applications, mobile devices, and hybrid work environments.
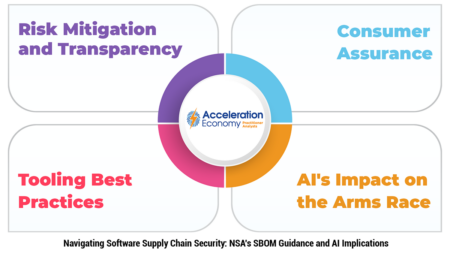
An exploration of the NSA’s software supply chain security guidance and how it can help organizations fortify overall cybersecurity.
In 2024, the challenges of AI adoption, cloud migration, and cultural shifts take center stage for CIOs striving to align IT with business.
A look at the dynamic state of AI adoption in the cloud through a Wiz report revealing trends, adoption rates, and the rise of power users in both managed and self-hosted AI services.
Lacework’s latest innovation, AI Assist, transforms cloud-native security by offering personalized recommendations, natural language interactions, and expedited remediation.
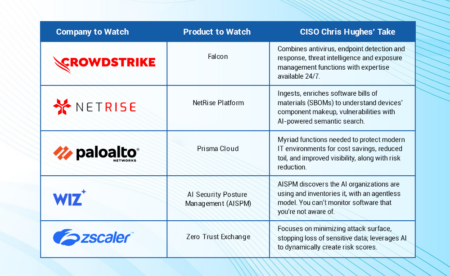
In this report, Chris Hughes identifies five products — from CloudStrike, NetRise, Palo Alto Networks, Wiz, and Zscaler — that equip CISOs to combat the latest threats.
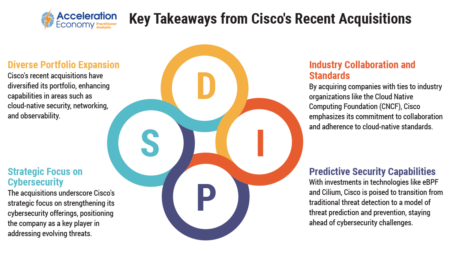
Cisco is positioning itself for the future of cloud-native cybersecurity and AI through acquisitions of Splunk and Isovalent.
Snyk’s report on AI-generated code security shows how developers, lured by accelerated production, are unwittingly overlooking risks.
AnalystGPT taps into over 10,000 reports, articles, and videos by Acceleration Economy practitioner analysts to answer questions about AI, cloud, cybersecurity, and data.
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
Discover the hidden risks embedded in AI code, including false security assumptions and a pattern of bypassing policies.
There is significant strategic value in looking at how cybersecurity threats are evolving and how that relates to strategic business plans.
For CISOs and security leaders, grappling with the global ramifications of the EU AI Act becomes paramount, necessitating a proactive stance.
Frank Domizio explores how IT leaders can ensure their organizations are protected from security threats in a way that also enables business growth.
A look at new guidelines for secure AI system development released by the Cybersecurity Infrastructure and Security Agency and the National Cybersecurity Center in the UK, emphasizing a holistic approach throughout the software development lifecycle.
Chris Hughes explains why sharing insights from threat intelligence with other senior execs can be a force multiplier in reducing organizational risk.