Aviatrix is a multi-cloud security company offering a centralized control plane to manage configurations, networking, and security across various cloud service providers.
zero trust
A federal watchdog group’s dareport exposes major flaws in Microsoft’s cloud cybersecurity, demanding urgent action from CEO Satya Nadella to address widespread shortcomings and restore customer trust amidst escalating cyber threats.
This guidebook offers insights on making zero trust a reality in our businesses, minimizing vulnerabilities that come with SaaS applications, mobile devices, and hybrid work environments.
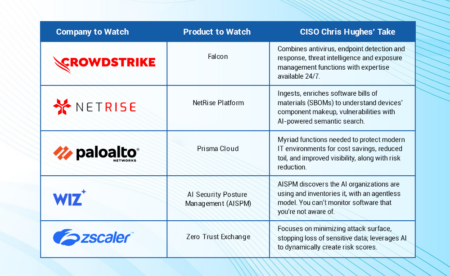
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
In this guidebook, practitioner analysts and CISOs define how to craft a secure foundation for businesses to thrive in today’s ever-changing digital economy.
The chief data officer (CDO) and chief information security officer (CISO) should agree on encryption, role-based access, zero trust security, and data retention for effective business decisions and risk mitigation.
Learn the three main ideas behind zero trust packet routing, which involve bringing identity to the cloud, automating policy creation, and emphasizing ongoing policy adaptability.
Fortinet’s “Cyber Threat Predictions for 2023” report examines the rise of ransomware, the mainstreaming of edge attacks, and the weaponization of AI.
Get a preview of “Selling to the New Executive Buying Committee,” an Acceleration Economy Course on vendor selection criteria for multi-cloud and SaaS cybersecurity.
This guidebook examines zero trust through the lens of business leaders and serves as a decision-making tool for creating a framework and implementing zero trust.
It’s essential that everyone in the workforce understand how to keep their mobile phones, laptops, and other endpoint devices secure, writes Chris Hughes.
Implementation of zero trust security for geographically distributed endpoints is critical in the age of remote work.
The Rubrik management platform provides data resilience, observability, and remediation. Find out what differentiates Rubrik.
Key RSA 2023 takeaways include a strong emphasis on AI defense, the push for an identity-centric security model, and management of the increasingly complex modern attack surface.
In a survey of 1,600 business and tech leaders, Rubrik finds high levels of concern about cybersecurity preparedness, and reveals the extent of ransomware demands.
The latest Growth Swarm podcast covers cybersecurity as a business enabler from the CEO perspective, the CMO perspective, and the industry perspective.
The big change of zero trust can be intimidating to some, but security leaders can tailor their communication to make the shift more palatable.
Implementation of zero trust principles, along with role-based access, will ensure robust data governance.
Metrics are a critical part of implementing zero trust.
There are many benefits to using the zero trust maturity model as a framework for cybersecurity planning and implementation, say Rob Wood.