New CX Trends data from Zendesk highlights the impressive benefits early adopters of AI technology are realizing while raising the key factors they must continue to address to sustain strong outcomes.
security
Microsoft MVP shares his copilot journey within the business apps community and discusses the importance of preparing a robust strategy covering data and governance when moving to AI.
A company-by-company breakdown of Cloud Wars CEO of the Year candidates, their strengths, and their companies’ latest wins.
Google Cloud’s ecosystem of advanced AI technologies and industry partnerships empowers businesses to drive productivity, innovation, and growth through strategic applications of GenAI, data management, and security.
Last week’s AI Copilot Preconference at Community Summit delivered a wealth of insight into the state of copilots. Top priorities: data, change management, and people.
Enterprise architect explains how document co-creation in Copilot saves hours and details potential new Copilot use cases addressing core business functions.
Tyler Predale shares how Flashpoint uses Gemini AI to enhance productivity, streamline tasks, and empower employees across departments.
During the AI Copilot Digital Summit, Adwait Joshi descibed the benefits of Microsoft Copilot for Security. Following this segment, CISO Chris Hughes shares his analyst perspective on the future of cybersecurity.
Oracle is focused on simplifying multi-cloud environments while delivering strong performance and reliability.
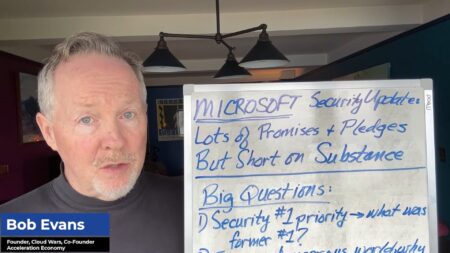
Microsoft faces scrutiny over its commitment to enhancing cybersecurity, as it announces new security priorities while grappling with past failures and ongoing challenges.
Copilots enable an interative model where humans and AI co-create; IBM ramps up focus on Microsoft Copilots; AI security — without agents.
The leadership of Arvind Krishna and others has successfully guided legacy tech companies like Oracle, SAP, and IBM through transformative changes, leading to significant market cap gains in the AI revolution.
Oracle advances the future of enterprise technology with integrated AI tools and secure solutions presented at CloudWorld 2024.
If Identity and Access Management (IAM) software goes down, business continuity takes a big hit. HYCU is addressing the problem for customers of Microsoft and other IAM platforms.
In a move to integrate AI into its products, Apple launched “Apple Intelligence” and “Privacy Cloud Compute” for enhanced privacy, with a beta release set for this fall.
Larry Ellison asserts Oracle will revolutionize cloud services by creating both the world’s largest AI data centers and ultra-compact, portable cloud data centers for individual customers, even on ships and submarines.
Analyzing Microsoft’s recent cybersecurity challenges, including deficiencies in its security culture, the introduction of the Secure Future Initiative, and efforts to prioritize security in light of growing scrutiny and the need to regain customer trust.
New data clean room app — integrated into the Snowflake Data Cloud — makes cross-company, cross-cloud data sharing secure and easily accessible.
Andi Gutmans, VP and GM for databases at Google, highlights a surge in customer interest in modernizing their database estates by transitioning from legacy to open-source databases, driven by flexibility and cost benefits.
Chris Hughes explains why sharing insights from threat intelligence with other senior execs can be a force multiplier in reducing organizational risk.