Google Cloud’s ecosystem of advanced AI technologies and industry partnerships empowers businesses to drive productivity, innovation, and growth through strategic applications of GenAI, data management, and security.
Search Results: open source (2071)
AI Ecosystem Report Ep 51: Meta and Mistral AI announce their biggest LLMs to date; Cohere secures funds to support enterprise customers; and Harvey’s copilot supports lawyers with legal functions.
The AI Ecosystem Pioneers as well as emerging startups haven’t slowed the pace of innovation, as the AI market continued its forward march over the past month.
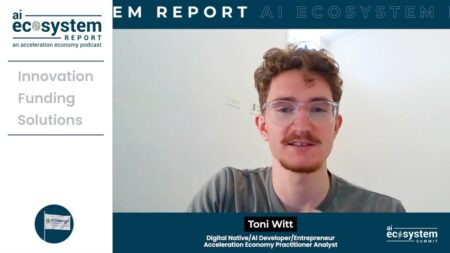
NVIDIA’s broad array of market-leading AI hardware and software, combined with an expansive partners ecosystem, secures its spot as the top provider of AI technology.
With its planned $4.6 billion HashiCorp acquisition, IBM aims to give customers the tools to manage hybrid cloud complexity in an AI-centric world.
Databricks’ AI Security Framework illuminates the path to secure and compliant AI adoption, addressing critical security risks across various stages of AI systems.
With Wiz CNAPP, CISOs embark on a new era of cloud security, leveraging integrated solutions to simplify operations and bolster defenses.
Apromore co-founder Marlon Dumas details where GenAI fits in customers’ plans, the need for predictive functionality, and why time to value is so important today.
AI Ecosystem Report Ep. 31: ServiceNow, Hugging Face, and Nvidia partner to develop open-access LLMs for code generation; Figure secures funding for building AI-powered humanoid robots; and Google releases Gemma models in partnership with Hugging Face.
CEO Thomas Kurian’s customer-centric approach, which he details in a one-on-one interview, has led to significant growth for Google Cloud, with Q4 revenue reaching $9.2 billion and a 25.7% growth rate.
Snyk’s report on AI-generated code security shows how developers, lured by accelerated production, are unwittingly overlooking risks.
The top 5 generative AI products to watch feature platforms to build GenAI and machine learning apps, produce content, govern AI, and accelerate automation initiatives.
Andi Gutmans, VP and GM for databases at Google, highlights a surge in customer interest in modernizing their database estates by transitioning from legacy to open-source databases, driven by flexibility and cost benefits.
With an expansive ecosystem strategy, IBM has once again asserted leadership around AI and its watsonx technology, taking a mature, differentiated approach.
Google Cloud emerges as the preferred choice for over 70% of generative AI startups due to its advanced AI capabilities, reliable infrastructure, and open-source commitment.
AI capabilities, generative AI customer count, and operating profits are just three of the reasons that Google Cloud replaced AWS on the Cloud Wars Top 10 list.
Discover why closing the loop by fixing code is essential to effectively combat the security risk of hard-coded secrets.
The cybersecurity innovator Snyk caters to developers, ensuring that their code is secure as it’s written, and that their open-source software is monitored continuously.
Bob Evans reviews Larry Ellison’s remarks as he made an appearance during the Oracle Database Summit to highlight three key topics.
New data from cybersecurity provider Chainguard captures what’s working, and the relative difficultly levels, of various software supply chain practices.