As cybersecurity strategy and technology continues to increase in complexity, organizations struggle with implementing effective governance. From security tooling and findings to prioritizing remediations to dealing with compliance reporting, the reality is there’s a lot to juggle in cybersecurity and doing so often feels like an insurmountable task.
Cybersecurity isn’t alone in struggling with complexity. Many tech sectors and business process owners are beginning to lean into the power of process mining, which combines data science and process management analysis to facilitate actionable intelligence. Cybersecurity is increasingly a data problem, and without making sense of all the data from various sources, it’s difficult to drive the security program in a unified direction. Cybersecurity process mining can change that, and Gutsy is leading the way.
Take a deep dive into the state of process mining with our course Process Mining in the Cloud Wars GenAI Era launching in late March. The course will define the category and business opportunity, the impact of GenAI, CXO evaluation criteria, and leading vendors’ technology. Register now.
Gutsy boasts an impressively experienced leadership team, consisting of the founders of the cybersecurity company Twistlock, acquired by Palo Alto Networks in 2019 for $410 million. In late 2023, Gutsy announced a major $51 million seed round of investment, despite many cybersecurity companies struggling to raise capital.
So, what does Gutsy do, and what is the promise of cybersecurity process mining?
Let’s take a look.
Ask Cloud Wars AI Agent about this analysis
Security Tool Sprawl
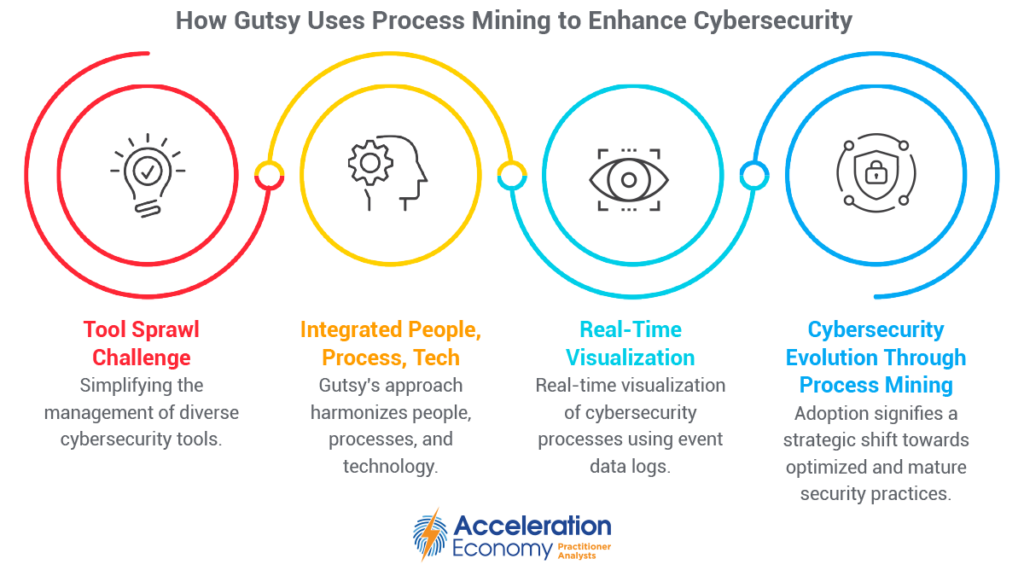
A major challenge facing the cybersecurity industry is tool sprawl. Due to the diverse and complicated nature of the threat landscape, organizations often end up managing tens or even hundreds of cybersecurity tools aimed at protecting the cloud, endpoints, identities, software, infrastructure, and more. The types and number of tools vary depending on the size, complexity, and maturity of the organization.
Tools don’t always integrate or utilize common data formats, making it difficult for security leaders to comprehensively understand their findings and insights. Further complications arise due to security teams’ finite time, staff, and expertise. These limitations often leave tools only partially implemented or configured, ultimately providing little real value. Teams can suffer from cognitive overload just trying to make sense of all of the various tools and their associated insights.
The People, Process, and Technology Paradigm
Combined with the tool sprawl challenge is the undeniable fact that cybersecurity isn’t just a technological problem. Most experienced security professionals recognize that cybersecurity is a combination of people, process, and technology, and often put them in that order of importance.
The best technologies, tools, and platforms will fail to deliver optimal security outcomes if they don’t have sufficiently documented and adhered-to processes and a competent, empowered, and impassioned workforce behind them. Due to the complexity of modern organizational structures and the seemingly endless surge in compliance requirements, many detailed processes are often necessary to unite all individuals and tools cohesively into a comprehensive strategy.
Cybersecurity Process Mining
This is where innovators such as Gutsy, looking to apply process mining to cybersecurity, enter the picture. Gutsy utilizes process mining to help organizations visualize how their various cybersecurity processes, tooling, and environments operate. It leverages event data logs to depict data flows and interactions.
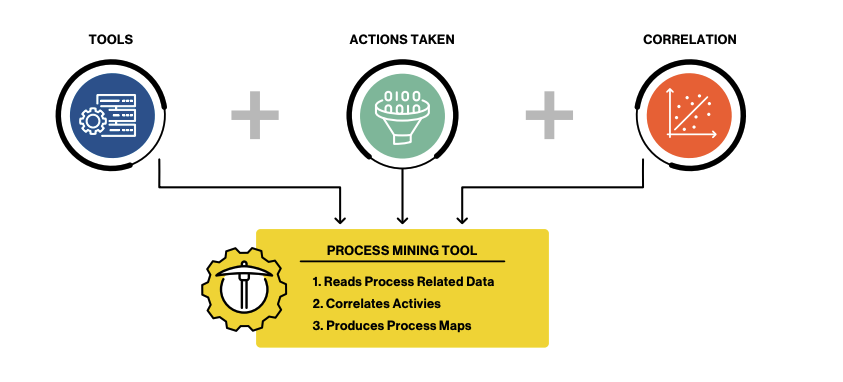
Even though organizations often have documented processes, these are abstract ideas that are hard to visualize, and they exist in disparate static documents. What if you could visualize those processes in action, within your enterprise infrastructure, demonstrating how the people, process, and technology paradigm is operating in reality? Not how it should be, but how it truly is.
Being able to visualize and understand how one’s technology stack, workforce, and processes are working together can help with risk identification. Further, identifying core problems, recognizing inefficiencies in security operations, and streamlining processes can enhance overall effectiveness. Utilizing process mining is a practical way to address these issues.
Process mining can also help with compliance. From pressures to properly inform the board around cybersecurity risk, increased calls for transparency from customers, and oversight from regulators such as the Securities and Exchange Commission (SEC), compliance is a core cybersecurity function. Being able to visualize cybersecurity processes in action can maximize adherence to compliance requirements, helping minimize organizational regulatory risks.
Conclusion
Cybersecurity as a practice and profession continues to evolve and mature, facing increased calls for data-driven, quantifiable insights as well as transparency and accountability. By leveraging innovative approaches such as cybersecurity process mining, organizations can move beyond making guesses about how efficiently their people, processes, and technologies are working and instead be able to provide data to support actions.
They can also begin to understand the real effectiveness of their cybersecurity tools and investments and determine where to make additional investments or even rationalize some of their tooling portfolio. Cybersecurity process mining is an example of our career field maturing; the most forward-leaning organizations and security leaders will increasingly look to adopt this innovative approach.











