In a previous analysis, we discussed how sharing threat intelligence across the C-suite can foster cross-collaboration, empower other key C-suite executives to mitigate risk, and also contribute to a culture of security. This analysis will showcase a subset of threat intelligence, tactical threat intelligence. Tactical threat intelligence is the process of collecting and analyzing technical data to identify and mitigate cyber threats with a focus on malware and specific behavioral threat indicators for malicious actors.
Threat Intelligence Areas
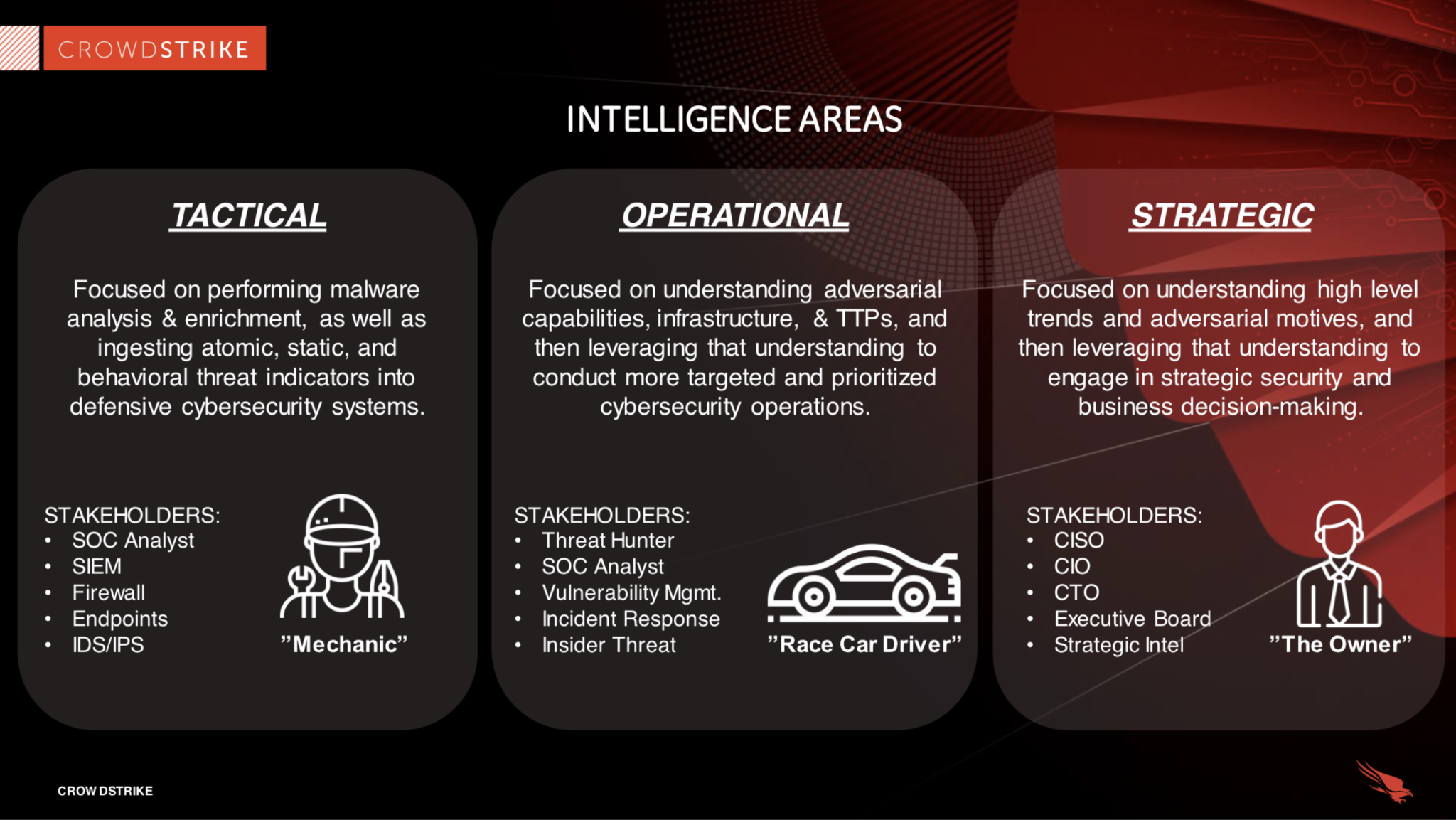
There are three main threat intelligence areas, as depicted by cloud security company Crowdstrike in the image below: tactical, operational, and strategic.
While operational threat intelligence centers on improving cybersecurity operations and strategic threat intelligence is largely about better business decision-making activities, tactical threat intelligence focuses on performing specific activities using insights such as threat indicators to improve the performance of security tooling. It can be used to enhance the performance of things such as web application firewalls (WAFs), intrusion detection/prevention systems, and security operations center (SOC) analysts.
Tactical threat intelligence sources can include data from a variety of sources such as network logs, system event logs, and threat feeds. By analyzing this data, organizations can gain insights into the tactics, techniques, and procedures (TTPs) used by cybercriminals and better understand the potential impact of these threats on their business.
Benefits of Tactical Threat Intelligence
One of tactical threat intelligence’s primary benefits is that it can help organizations mitigate risk to their business by identifying and responding to threats in real time. I’ve had situations in my career where quick response made the difference between a minor incident or what could have been the exposure of several thousands of individuals’ personal data.
For example, if an organization detects unusual network traffic that could indicate a cyber attack, it can use technical threat intelligence to investigate the threat and take appropriate action to prevent further damage. This is where organizations are able to use the identified TTPs to determine if the behavior they are observing aligns with malicious actors’ behavior seen in the wild.
Another key benefit of tactical threat intelligence is that it can help organizations to prioritize cybersecurity efforts such as security architecture, engineering, and operations. It can be used to better architect environments, design secure systems and bolster security operations to mitigate malicious activity. By analyzing threat data and identifying the most significant threats, organizations can focus their resources on the areas of greatest risk.
Leveraging Threat Intelligence
CISOs and other cybersecurity professionals can leverage tactical threat intelligence in a variety of ways to protect their organizations from cyber threats.
One common approach is to use threat intelligence platforms such as IBM X-Force or LookingGlass Cyber Solutions, which can help to automate the process of collecting and analyzing threat data. They can also help identify threats in real time and provide actionable insights that can be used to respond to threats quickly.
Another is to use threat intelligence feeds, which provide up-to-date information about known threats and their potential impact. These feeds can be integrated with security tools such as firewalls and intrusion detection systems to help organizations respond to threats more effectively.
In addition to these tools, organizations can also leverage threat intelligence to improve their incident response capabilities. By understanding the TTPs used by cybercriminals, organizations can develop incident response plans that are tailored to specific threats such as ransomware, malware, or data exfiltration. This can help to minimize the impact of cyber attacks and reduce the time it takes to detect and respond to them.
Finally, organizations can use technical threat intelligence to improve their overall cybersecurity posture. By analyzing threat data and identifying vulnerabilities, organizations can take proactive steps to mitigate these risks and reduce their overall exposure to cyber threats.

Which companies are the most important vendors in cybersecurity? Check out
the Acceleration Economy Cybersecurity
Top 10 Shortlist.
Final Thoughts
In conclusion, tactical threat intelligence is a critical tool for organizations looking to mitigate risk to their business in today’s complex cyber threat landscape. By collecting and analyzing technical data, organizations can gain insights into the tactics, techniques, and procedures used by cybercriminals and take proactive steps to protect their business from these threats.
CISOs and other cybersecurity professionals can leverage a variety of tools and techniques to incorporate technical threat intelligence into their cybersecurity strategy and stay ahead of evolving threats. By doing so, they can help to ensure the security and resilience of their organization in the face of ever-changing cyber threats.
Want more cybersecurity insights? Visit the Cybersecurity channel:











