In the last few years, the tech industry has experienced a massive uptick in vulnerabilities. This increase is partly due to new software supply chain disruptions and risks in widely used open-source packages. Even as sophisticated attacks emerge daily, hackers continue to leverage older, known, and unpatched vulnerabilities to wreak havoc on insecure systems.
Trustwave recently released an interesting report titled “Decade Retrospective: The State of Vulnerabilities.” The report rehashes major exploits over a 10-year timespan between 2011 and 2021. As the data shows, risks concerning web-based applications have dominated the last decade. Additionally, medium-severity vulnerabilities have risen exponentially since 2017.
Below, I’ll highlight the report’s key takeaways and consider how organizations can use this knowledge to better arm themselves against future threats. We’ll also revisit the top 10 most significant vulnerabilities from the last decade and anticipate what the coming decade will hold.
Summarizing 10 Years of Vulnerabilities
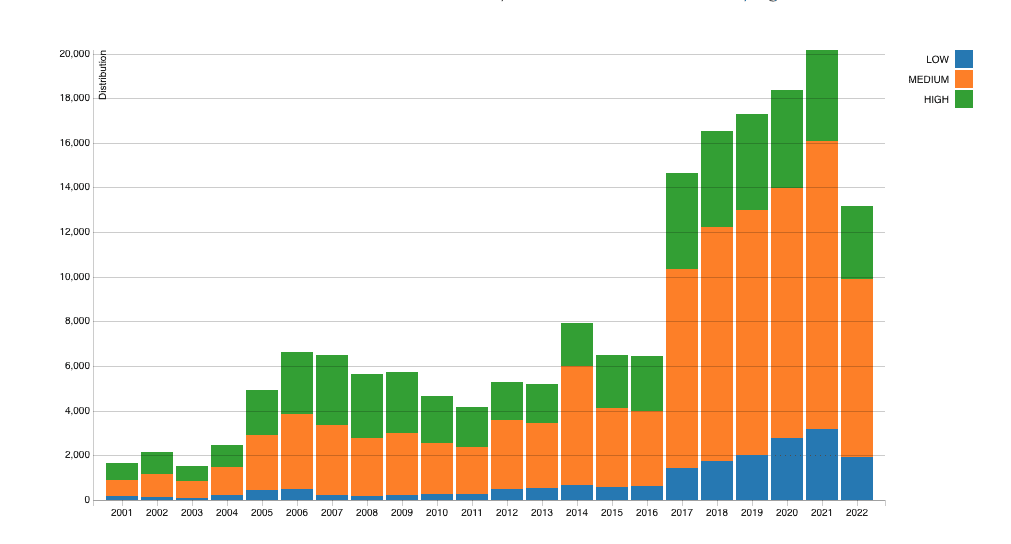
The National Institute of Standards and Technology (NIST) operates the comprehensive National Vulnerability Database (NVD), which showcases a severity distribution of software vulnerabilities from 2000 to the present day. The NVD data shows a consistent overall trend of increasing vulnerabilities throughout the last decade, with a spike in 2017 and a hockey-stick growth since.
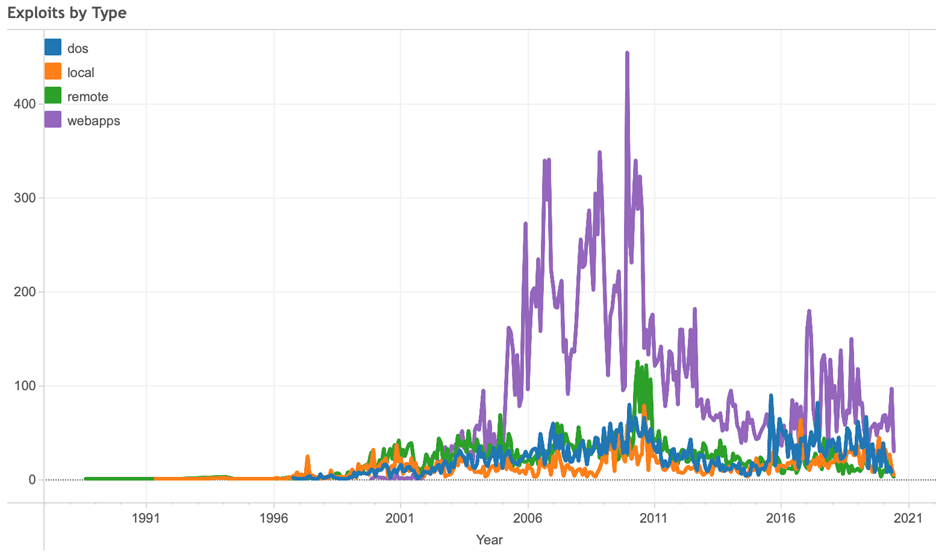
If we turn to data produced by Exploit Database, we can see that vulnerabilities have specifically targeted web applications over the past decade. Web application vulnerabilities are outnumbering DOS, local, and remote attack types.
Another source, Common Weakness Enumeration (CWE), continually lists cross-site scripting (XSS) as a staple vulnerability. This is consistent with other research, which marks XSS as a top web application risk; followed by cross-site request forgery (CSRF); SQL injection (SQLi); server-side request forgery (SSRF); local file inclusion (LFI); and remote code execution (RCE), among others.
The 10 Most Significant Exploits of the Last Decade
Exploits can cause significant damage to a company’s reputation and lead to hefty financial losses. IBM’s “Cost of a Data Breach Report,” now in its 17th year, found the average data breach cost to be $4.35 million in 2022, up more than 12 percent from two short years ago. Over the past decade, certain vulnerabilities plagued the industry more than others. In their retrospective, Trustwave listed these top 10 exploits:
- SolarWinds Hack
- EternalBlue exploit
- Heartbleed
- Shellshock
- Apache RCE and Equifax breach
- Meltdown
- BlueKeep
- Drupalgeddon
- Sandworm
- Ripple20
To add to this list, the Apache Log4j vulnerability, a remote code execution (RCE) risk discovered in late 2021, is estimated to affect upwards of 3 billion devices. Permutations of the vulnerability continue to emerge — for example, Spring4Shell has been found to be similarly devastating under the proper conditions.
Why Unpatched Vulnerabilities Persist
Surprisingly, attackers continue to exploit known vulnerabilities in the wild — fixes and patches are usually available but are often not utilized by all clients. As a result, there are still many vulnerable, publicly exposed servers on the Internet. So, why does this problem continue? According to the Trustwave retrospective, unpatched vulnerabilities likely persist, in part, due to a lack of knowledge. Organizations may not have the proper security observability to monitor all their services. Without a complete inventory of an enterprise’s software footprint, auditing every piece of potentially vulnerable code can be difficult.
Another reason vulnerabilities might persist is a slow reaction time to zero-day exploits. The Project Zero team at Google found that software vendors take, on average, 15 days to patch a vulnerability that is being used in active attacks. Depending on the type of exploit, this could be ample time for bad actors to discover the vulnerability and take action against unpatched victims. Then, of course, there is the time between a patch release and the client implementing the fix. Studies estimate that it takes two months, on average, for an organization to patch known critical risks. This delay is possibly extended out of fear of the patch interrupting the company’s workflow.
It’s always good to take a retrospective after a single security incident. The same thinking applies to broader trends throughout the industry. These vulnerability trends we’ve witnessed throughout the previous decades will undoubtedly inform the future of cybersecurity efforts. Storied attack types will continue to threaten organizations as new, more nuanced vulnerabilities introduce themselves alongside novel technology adoption.
Armoring Up for the Next Decade of Zero Days
Looking to the next decade, companies should prepare for a new class of zero-day exploits. For example, the adoption of a new cloud-native stack is currently underway throughout most enterprises. While containers, Kubernetes, and other cloud-native architecture triumphs over elasticity and reliability, they carry the potential for misconfigurations, broken access control, leaked secrets, and other novel cloud-native threats. One minor leak in the cloud infrastructure could expose it to a wide surface area of attack, leaving an organization prone to ransomware or cryptojacking.
Increased work-from-home policies also invite new frailties concerning remote access, causing CISOs to play a careful balancing act between flexibility and security. In this new paradigm, zero-trust architecture has emerged to treat all request patterns with the same level of scrutiny, no matter if they’re an internal employee or an external user.
Simultaneously, open data and application programming interfaces (APIs) are on the rise, underpinning the need for tight access control to avoid breaking the rule of least privilege. To protect today’s interconnected mesh of services, some are turning to artificial intelligence to scan requests for bad actors. In this way, systems could automatically prevent those with malicious intent from performing reconnaissance and introspection.
To sum up, the findings from these reports reinforce the need to patch compromised servers, use active threat monitoring, and prepare for quick responses to future zero-day exploits.
Want more cybersecurity insights? Visit the Cybersecurity channel:







