Building on its longstanding cloud strengths, Google Cloud has similarly staked out a leadership position in AI based on tech innovation, partnerships, and customer successes.
Standard Chartered Bank and SAP executives delve into the bank’s global transformation journey, focusing on technology’s pivotal role and strategic priorities. They discuss collaborative innovations driving financial and operational efficiencies across diverse markets and regulatory landscapes.
Snowflake delivers mandatory multi-factor authentication (MFA) option so customers can exert stronger access controls.
With its new chatbot, Databricks lets customers tap natural language to query data, generate code, and more, while ensuring contextually accurate data.
Larry Ellison’s commitment to embed GenAI across Oracle’s expansive product portfolio positions his company as a leader in the AI ecosystem, building on its history of tech innovation.
As hyperscaler rivals Microsoft and Google Cloud partner with Oracle for multicloud database services, the pressure grows on Amazon/AWS and Andy Jassy to do the same.
Equipment manufacturer Takeuchi extols the benefits of timely, reliable views of data in Qlik dashboards, which replaced spreadsheet-based tracking.
At its Qlik Connect customer conference, the analytics and data quality provider details how it’s integrating Talend, improving integration, and supporting unstructured data with GenAI.
The battle between SAP and Salesforce has shifted for supremacy in the enterprise apps space to not just focus on apps or AI but on data.
Discover how to ensure data health — which involves data integrity, quality, and governance — to prepare for your next cloud and AI migration.
HYCU and Dell expand their respective ecosystems around data protection technology by extending their integration efforts to new platforms.
The report delves into the importance of Product Lifecycle Management (PLM) platforms in managing the entire product journey from creation to service, and how Propel’s solution stands out from other vendors in the space.
With LLMs bringing new prospects for innovation, Databricks launches its open, general-purpose model, DBRX.
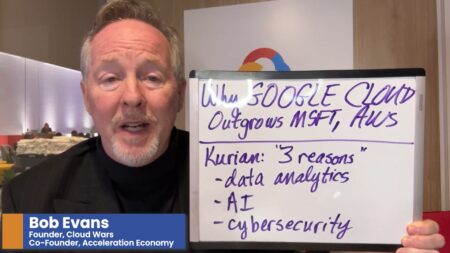
During Google Cloud Next, CEO Thomas Kurian cites three reasons why Google Cloud is growing faster than its competitors: data analytics, AI, and cybersecurity.
AI Ecosystem Report Ep 34: NVIDIA and Hippocratic AI partner to develop AI healthcare agents; BigID secures funds for its AI-powered data security offerings; and Elon Musk launches Grok, a real-time chatbot for the X platform.
AI Ecosystem Ep 33: Fluent provides AI data analytics; Databricks acquires Lilac for improved data pipelines; and Cohere partners with Accenture for enterprise AI adoption.
This report highlights IBM innovations that result in the Cloud Wars Top 10 company being listed on 5 out 8 categories for products to watch in 2024 by our practitioner analysts.
AI Index Ep 28: Super Bowl commercials highlight generative AI; Perplexity raised $73.6M; and Pecan AI develops predictive-model offerings.
Transportation Visibility Platforms have made big strides in providing visibility into the entire supply chain across all modes of transportation — a critical benefit amid global upheaval.
Partnering with Soracom, Couchbase makes it easier for customers to connect IoT devices in diverse geographical locations and remote areas where connectivity is often difficult.