In the conversation around vulnerability management and scoring, one often overlooked aspect is the vulnerability’s actual exploitability. Organizations generally prioritize vulnerability based on criticality such as critical or high, as well as scores, often defined by sources such as the Common Vulnerability Scoring System (CVSS). The problem with this method of vulnerability prioritization is that it doesn’t account for whether or not the vulnerabilities are actually exploitable. This leads to organizations focusing on vulnerabilities that might not actually pose any risk. The Exploit Prediction Scoring System (EPSS) is an emerging system that hopes to help solve this problem.
The Aim of EPSS
EPSS aims to help security practitioners and their organizations improve vulnerability prioritization efforts. There are an exponential number of vulnerabilities in today’s digital landscape, and that number is only increasing due to factors such as increased digitization of systems and society; increased scrutiny of digital products; and improved research and reporting capabilities. EPSS points out that organizations generally can only fix between 5%-20% of vulnerabilities monthly.
There is also the reality that fewer than 10% of vulnerabilities that get published are ever known to be exploited in the wild. Additionally, there are longstanding workforce issues at play: The annual ISC2 Cybersecurity Workforce Study shows shortages exceeding two million cybersecurity professionals globally. Taken together, all these factors warrant organizations having a coherent, effective approach to aid in prioritizing vulnerabilities that pose the highest risk to their organization and thereby avoid wasting limited resources and time.
The EPSS model aims to provide support by producing probability scores that a vulnerability will be exploited in the next 30 days and the scores range between zero and one or 0% and 100%. To provide these scores and projections, EPSS utilizes data from various sources such as the MITRE CVE (common vulnerabilities and exposures) list; data about CVEs such as days since publication; and observations from exploitation-in-the-wild activity from security vendors such as AlienVault and Fortinet.
Coupling EPSS and CVSS
The EPSS team published data to support its approach of using not just CVSS scores but coupling them with EPSS scoring data to lead to more effective vulnerability remediation efforts. For example, many organizations mandate that vulnerabilities with a specific CVSS score or higher must be remediated, such as a seven or above. But this prioritizes vulnerability remediation based on only the CVSS score, not if the vulnerability is known to be exploited or not. Coupling EPSS with CVSS is more effective because then this method prioritizes vulnerabilities not merely based on their severity rating, but also if they are known to be actively exploited, letting organizations address CVEs that pose the greatest risk to the organization.
A Closer Look at EPSS
EPSS focuses on two core metrics which are efficiency and coverage. Efficiency is a look at how organizations are using resources to resolve the percentage of remediated vulnerabilities. EPSS points out that it is more efficient for most of an organization’s resources to be spent remediating mostly known-exploited vulnerabilities, as opposed to random vulnerabilities based on only severity scores via CVSS. Coverage is a look at the percentage of exploited vulnerabilities that were remediated.
To show its approach’s efficiency, EPSS conducted a study in 2021 utilizing CVSS v3 base scores, EPSS v1, and EPSS v2 data. It looked over a 30-day period to determine the total number of CVEs; the number of remediated CVEs; and the number of exploited CVEs. As you can see from the diagram below a couple of things jump out. Initially, the reality is that the majority of CVEs simply aren’t remediated.
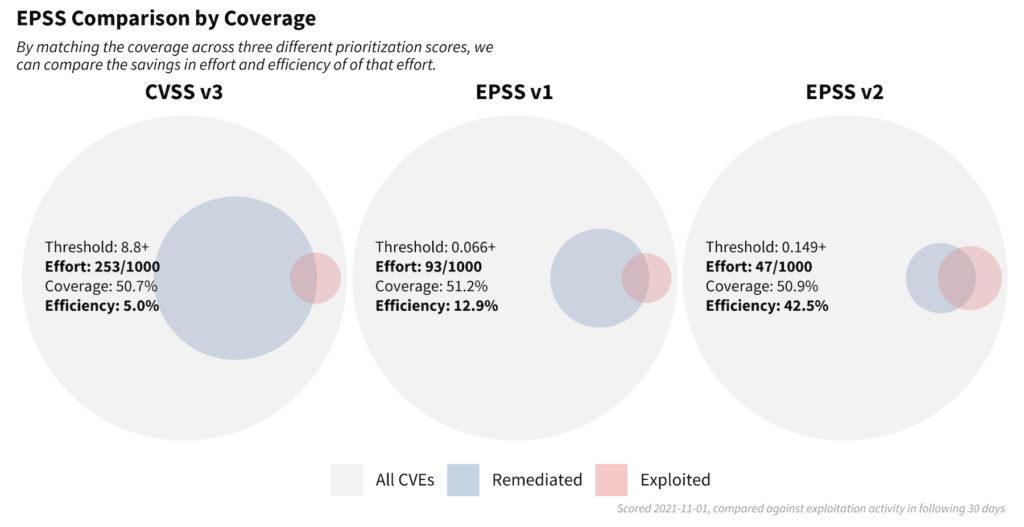
Secondly, the number of exploited CVEs that are remediated is just a subset of the total remediated CVEs. This means that organizations don’t remediate most CVEs, and among those they do, many aren’t actively known to be exploited and potentially don’t pose the greatest risk. It also demonstrates that the EPSS v2 further improves the efficiency of vulnerability remediation efforts by maximizing the percentage of exploited vulnerabilities that are remediated.
Final Thoughts
When organizations have resource challenges with cybersecurity practitioners, it is crucial to maximize their return on investment by having the resources focus on the vulnerabilities that pose the greatest risk to the organization. Ultimately, EPSS is trying to help organizations make more efficient use of their limited resources and improve their effectiveness in driving down organizational risk.
Want more cybersecurity insights? Visit the Cybersecurity channel:











