AI Index Report Ep 16: HeyGen uses AI and deep fakes for language translations; Wraithwatch gains funding for generative AI threat detection; and Microsoft launches its lightweight phi-1.5 model.
vulnerability
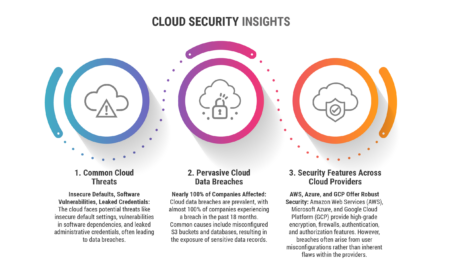
The big three cloud service providers AWS, Azure and Google Cloud share but also differ on features and vulnerabilities.
OWASP has updated CycloneDX to support machine learning models, as the next generation of AI continues to enhance technology.
Discover the top 10 Low-Code/No-Code vulnerabilities and how to secure rapid development environments.
There are several security risks associated with generative AI, including AI-powered social engineering attacks and evasion of traditional security defenses.
Process mining has several potential cybersecurity applications including incident investigation, anomaly detection, and detecting insider threats.
Fortinet’s “Cyber Threat Predictions for 2023” report examines the rise of ransomware, the mainstreaming of edge attacks, and the weaponization of AI.
GitGuardian and Snyk join forces to strengthen cloud-native security, enhance their developer-centric approach, and drive early risk mitigation in software development.
Snyk and GitGuardian, two prominent security tools providers, collaborate to tackle cloud-native security challenges and bolster cybersecurity measures.
Bill Doerrfeld explains how AI is improving endpoint threat detection and accelerating response times.
There are unique endpoint security challenges associated with cloud-based systems. Here are some strategies to address them.
Leveraging threat intelligence for operational needs can make organizations more effective and adaptable in modern cybersecurity operations.
Bill Doerrfeld analyzes the state of modern CI/CD security, reviews the most common risks, and offers some safeguarding suggestions.
Rob Wood explores how organizations should think about generative AI models from a risk perspective, with a special focus on the conversations between security leaders and the C-suite.
Cybersecurity data can empower C-suite executives to make informed decisions, protect their organization, and drive business growth.
As sustainability becomes a key focus for businesses and critical infrastructure, organizations must also prioritize cybersecurity and secure data standards to safeguard emerging technologies like IoT and OT devices from evolving cyber threats.
Maturity models serve as roadmaps to help organizations successfully navigate their zero-trust journey. Rob Wood breaks down the benefits of one model’s iterative approach.
An in-depth look at automated vulnerability scanning within financial software, how it works, as well as top tools and best practices to get the job done.
Endor Labs released a report that identifies the top 10 open source software risks, including known vulnerabilities, compromised legitimate packages, untracked dependencies, and more. Chis Hughes explains.
Multi-cloud environments come with unique challenges, and analyst Rob Wood provides best practices for reducing security threats through training for employees with access to cloud resources.