Anthropic uses actual attacks against its own software to lay out specific ways that threat actors are leveraging AI to further their goals. Report serves as a troubling call to action for vendors, partners, and customers.
Ransomware
If Identity and Access Management (IAM) software goes down, business continuity takes a big hit. HYCU is addressing the problem for customers of Microsoft and other IAM platforms.
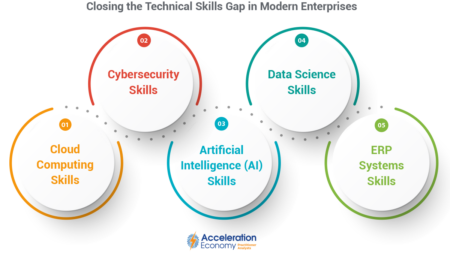
In order to prepare companies for the future of technology-driven business, it’s incumbent upon CIOs to identify and actively address the most critical tech skills gaps.
In 2024, the challenges of AI adoption, cloud migration, and cultural shifts take center stage for CIOs striving to align IT with business.
The increasing adoption of cloud services, particularly software-as-a-service (SaaS), has reshaped the role of the chief information security officer (CISO).
Fortinet’s “Cyber Threat Predictions for 2023” report examines the rise of ransomware, the mainstreaming of edge attacks, and the weaponization of AI.
These two complementary cybersecurity practices, when combined, enable organizations to quickly and effectively identify and mitigate potential cyber threats.
In this special “on location” minute, Paul Swider shares his impressions from the third day of the HIMSS 2023 Global Health Conference and Exhibition in Chicago.
Knowledge is power, and in the world of cybersecurity, the threat intelligence lifecycle is key to unlocking that power.
Implementation of zero trust principles, along with role-based access, will ensure robust data governance.
HYCU’s Protégé revolutionizes data protection by unifying data silos, providing backups, recovery measures, ransomware protection, and migrations through a single dashboard.
New data from Palo Alto Networks’ incident response team highlights the expanding set of extortion tactics being used as part of ransomware attacks.
The Biden-Harris administration unveiled an updated National Cybersecurity Strategy to standardize cybersecurity practices across agencies and encourage market accountability.
Environmental, social, and governance frameworks are on the rise, and they must be crafted with enough security considerations to ward off increased cyber threats.
These six cybersecurity practices can help board members create robust protocols to protect their organizations against diverse threats and attacks.
AI and automation can protect against financial and reputational losses from data theft and ransomware in financial software, writes Bill Doerrfeld.
CISO Frank Domizio looks at common security vulnerabilities in the retail industry and offers practical ways to mitigate them and boost resilience.
The shift to renewable energy leaves oil, gas, and electrical infrastructure vulnerable to threats such as ransomware, DDoS, and more, CISO Chris Hughes explains.
CISO practitioner analyst Chris Hughes emphasizes why today’s CISOs need to prioritize their agenda to quantify risk, embrace zero trust, and fight talent burnout
HYCU founder and CEO Simon Taylor shares his perspective on hybrid/multi-cloud, ransomware, and keeping customers’ data safe.