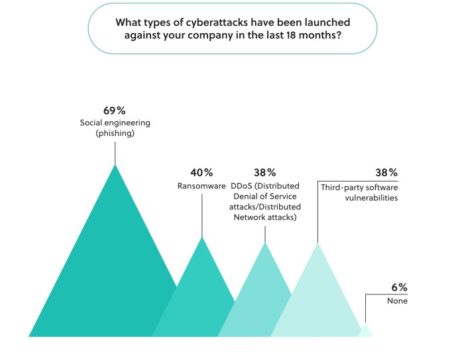
It is important for everyone in an organization to use data responsibly. This playbook offers guidance on how to format data to protect confidential, personally identifiable, and regulated data from being inappropriately accessed for various use cases. By de-identifying personal identities from being revealed, you can preserve the privacy of your customers, employees, and partners.
Learn how you can accelerate data safely and securely with dynamic data access policies. This paper will dive into:
What is Data De-Identification?
How to De-Identify PII to Speed Time-to-Insight for your Analysts
De-Identification for Data Analytics
Identify Trends with Partially Tokenized or Masked Data
Format Preserving Tokenization
Non-format Preserving Tokenization
Partial Masking
And more…
Implementing data de-identification with a dynamic policy enforcement solution such as Okera is not hard. By taking a practical approach to data de-identification, you will be more effective and your job will be much easier.