Good insights start with good data, and knowing what data to pull from your BC / NAV system, and how, makes all the difference. There are a lot of options available – XMLports, RapidStart Services, OData feeds, Excel – but what should you and your users employ for which purposes? We’ll start with real examples of each, then drill down into RapidStart to ensure you have a thorough understanding of this invaluable tool. We’ll address when and when not to use Configuration Packages, a step-by-step guide of how to create and modify Configuration Packages, and how to use the Configuration Worksheet.
Some companies have allowed a large number of workers to work remotely in the past, others have not until the Coronavirus arrived. Security and access to data, like the rest of your business processes in these challenging times, needs to now be looked at a bit differently. In this webinar, we will review the steps you and your company can put in place to ensure application and user security is not compromised with a remote work force. The good news is that more than likely your company probably has many techniques in place already, or in place and ready to easily implement. However, there are some controls that are often overlooked, and a since ‘a chain is only as strong as its weakest link,’ it is critical all security controls are addressed accordingly. We will highlight these commonly overlooked controls as well in this webinar.
Microsoft Power Query is the transformation engine in Power BI. This is the engine that you do all data preparation before loading data into the model. This is the keystone of your Power BI solution. In this session, you will learn what Power Query can do. You will learn how M, the language behind the scene of Power Query, can be more beneficial than the Power Query graphical interface.
Take a peek at the results and insight to the User Group Community Hack4Good virtual event that was held at Summit Europe: 27 June 2020!
We get the most value from Power Platform when we truly embrace it as a platform. In other words, while the component parts — Power BI, PowerApps, Flow, Common Data Service, and even Dynamics — are incredible tools in their own right, the more we knit them together, the more valuable they become.
But how do larger organizations truly adopt that platform at scale? How do we maturely infuse enterprise management, governance, and best practices into our adoption such that we empower our business users to buil
Presented by: @Kristine Dyess
As Power Pivot and Power BI consultants at PowerPivotPro, we see a lot of data models. We will review data model best practices and reasons why one approach may be better to adopt versus another approach. We will explore data models built in a traditional database environment like SQL and data models built using Get Data/Power Query. Join me for tips and tricks that will enable you to review your existing data models and ensure you’ve got good data models!#UnifiedOperations#CustomerEngagement#Intermediate
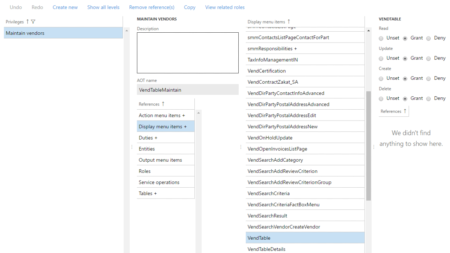
How do you know who has access to what? What are the best practices for managing your BC/NAV security? We’ll discuss how to create a good process to make sure employees can do what they need to and not what they aren’t supposed to. This session will cover the steps required to set up a new user in BC/NAV. We’ll also review the processes to assign permissions, manage user groups, set up warehouse security and how to create customized permission sets including a demonstration of the permissions recorder. Bring your questions, real life stories, and be prepared to share how you manage BC/NAV security in your company. This session will combine How-To presentations with interactive discussions to share best practices and fresh ideas.
Learning Objectives:
How to create a new user.
How to assign permissions to users.
How to create and manage permissions.
Join fellow users in your quest for certification with Microsoft Dynamics 365! Study Group sessions are round table discussions across a variety of topics and themes applicable to the Microsoft Certification listed. Please review the following topics for this week’s discussion on the MB200 Certification (Microsoft Power Platform + Dynamics 365 Core): Implement Security.
Importing Excel files into D365 F&O
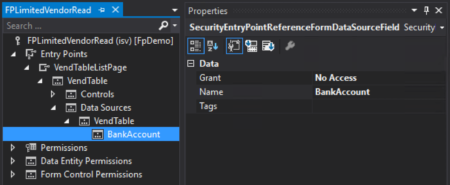
Learn how to set up field level security in D365FO.
Do you want to build a new list, but aren’t sure what tables to use to build it? During this session, we will walk through some of the best ways to figure out what tables to use. We will also look at how you can figure out how to link them and which order to use them in.
How do you tighten up security in Microsoft Dynamics 365 Business Central and NAV? We cover this question in this webinar to help companies enhance their security to satisfy auditors’ requirements and more. IT managers, accounting managers and other power users (e.g. controllers) will find this topic of particular use. You will hear all the key notions explained and shown in the system.
A lot!
Are you unsure how to create a new company in Microsoft Dynamics NAV? Want to know some easy tips on how to copy an existing company?
In this webinar, we will discuss some secret tips that you may or may not have known about Microsoft Dynamics NAV.
Learn about Row Level Security patterns, Static Row Level Security, Dynamic Row Level Security, and many variations of the dynamic RLS. You will learn about user profile security scenarios, and hierarchical access levels.
Join Nicole Albertson to walk through the templates available on the eOne Website for SmartList Builder. We will also take a few of them and walk through how they were created and how to figure out how they were built.
Data repair almost always has to happen at some point, what are the best practices and how do I repair the most common issues! And, dang it, what could be causing this! Learning Objectives: Upon completion participant will be able to understand different data issues that occur in Dynamics GP, understand the best places to find resources to assist in repairing common issues and understand the best practices around data repair in Dynamics GP.
This virtual panel discussion series will feature brief, informative yet interactive discussions in a 30 minute or less format to help you take in and learn some key features and best practices while using Dynamics 365 and CRM. These panels will consist of Dynamics 365 CRM end-using members and subject matter experts across the Dynamics 365 and CRM Community who will share a tip or best practice and field your questions thereafter.
In this webinar, we are going to see how you can store documents in SharePoint Online and how we can secure those documents through its security features. To use the document management functionality, you need to enable the server-based SharePoint integration on a site collection in SharePoint Online. Note that installing the Dynamics 365 list component was previously used for earlier versions of SharePoint on-premises and is not required for SharePoint Online and later versions of SharePoint on-premises.
With defensive programming, the main idea is that if a function is passed bad data it won’t be hurt, even if the bad data is another function’s fault. More generally, it’s the recognition that programs will be modified later on and will have problems, and that a smart developer will write their code to account for this. In this session you’ll learn how to protect yourself from the cold, cruel world of invalid data, events that can “never” happen, and other developers’ mistakes.