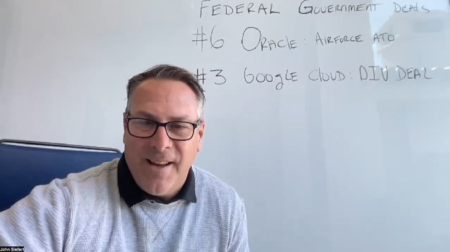
John Siefert fills in today to provide insights and perspectives around cloud vendors that have landed Federal Government Deals.
Review the top cybersecurity frameworks from NIST, CIS, CSA, ISO, and AWS. By following these benchmarks, you can improve your organization’s security.
Follow these benchmarks to improve your cybersecurity.
Acceleration Economy Analyst Chris Hughes shares 5 preventative measures to increase your cybersecurity footing.
The future and foundation of the Metaverse is dependent on giving the next generation new opportunities and breaking traditional barriers.
Lightning struck with Google Cloud’s recent deal with the Defense Innovation Unit to expand cybersecurity initiatives for the public sector.
Cybersecurity and the metaverse are both changing quickly. Explore the possibilities of cybersecurity within the context of the metaverse.
As the world is powered by technology and a digital economy, cybersecurity is vital to protecting and creating business value.
Software built nowadays leverages open-source software, which alleviates the need to rebuild something that already exists.
CISO & Acceleration Economy Analyst Robert Wood defines the 5 steps to protecting today’s digitally driven business from ransomware threats
What are the consequences, good or bad, of this mad dash into the metaverse? Like the gold rush of yesteryear, we are just at the beginning of new frontiers. In this Back @ IT episode, Kieron Allen joins to explore the untapped potential in the metaverse.
In this Analyst Predictions episode, the Analyst Network talks through the future of cybersecurity culture and risk mitigation.
Metrics are essential to running any security program — especially when developing a vulnerability management program.
With further adoption of Work From Anywhere, it’s critical that businesses understand the cybersecurity implications that come with it.
Cybersecurity Battleground brings together the top minds from the vendor and analyst communities to debate the opportunities and challenges of managing cybesecurity as a business…
7 Cyber Security Startups to Watch in 2022
With an abundance of cybersecurity tools, vulnerability management can benefit from simplifying the user experience.
Mental health apps are an important tool for many users, but how close are many developers from overstepping the mark with data privacy?
Cloud computing has led to a paradigm shift involving the increased use of Infrastructure-as-a-Code (IaC) through codification.
With the development of new technologies, the cybersecurity landscape requires a new tool to address potential vulnerabilities.
With a lack of standards for risk assessment, cybersecurity tools may be leading to more confusion when determining risk prioritization.