Robert explains why communication is key to getting security, legal, sales, and engineering teams on board with a DevSecOps strategy shift.
In Ep. 3 of the Acceleration Economy Minute, Kieron references the work of fellow AE cybersecurity analysts who discuss how and why organizations must expand on their approach to defense.
Threat hunting is often thought of as something one does to uncover as yet undetected threats in an organization. But there’s also attack-specific threat hunting, which, analyst Chris Hughes explains, is essential when responding to security breaches.
From victim and media notification to legal liabilities and government considerations, the many issues that arise after a security breach are more easily addressed with the help of a lawyer. Frank explains why.
Analyst Bill Doerrfeld discusses the benefits and drawbacks of low-code/no-code with CEO Prashanth Chandrasekar, giving examples of how the approach both widens businesses’ horizons and limits them.
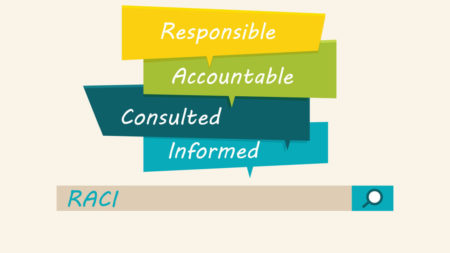
The first article in a series on the top 10 things to do if you’ve been breached discusses RACI (responsible, accountable, consulted, informed), a framework for defining roles and responsibilities in projects or processes.
In this Data Modernization Battleground moment, Chris says that cybersecurity professionals must understand data inventory, how businesses are using data, and who has access to data.
Analyst Chrus Hughes takes a look at EPSS, a new approach to evaluating vulnerability that takes into account not only criticality and scores, but also exploitability.
Wayne recaps Data Modernization Battleground sessions with Teradata and Okera, which discussed their data analytics for multi-cloud and data security solutions.
From hackathons and gamification to champion programs and callouts, there are many ways for security teams to build essential relationships with development teams.
Janet looks at this year’s Verizon Data Breach Investigations Report (DBIR) and singles out a few facts that can help organizations evaluate risk in partnership strategy.
Chris provides takeaways from the Cyber Safety Review Board’s recent Log4j incident report.
Cybersecurity has evolved beyond the “office of ‘no'” to a true business enabler that requires an on-going vigilant effort to keep a resilient security posture
Bill Doerrfeld speaks with oak9 Co-founder Aakash Shah about ways to reduce known and unknown vulnerabilities brought on by open-source software.
Since the public sector is known to be risk adverse, In the Cloud Wars Expo Moment, Nicholas Smith discusses the public sector’s tendency to be risk-averse, which is why Oracle bakes security into all of its cloud stacks.
As Bill explains, continuous delivery/deployment scenarios require special and specific security — especially in industries that handle sensitive personal and financial data.
In this Cloud Wars Expo Moment, Joe Wilson, CTO for Americas, Workday, explains the never-ending need for privacy and security in the hospitality industry, and why the company offers five core principles in its technologies.
In Ep. 9 of the Cutting Edge podcast, Leonard Lee explains why customers have a growing concern about privacy at the edge, and offers some intriguing solutions to the issue that edge computing can provide.
Penetration testing is an inherently manual process and runs in contrast to the DevSecOps movement, so where does it fit in? Robert Wood delves into it.
Data is the lifeblood of every business today but requires strategy, security, and governance to drive insights and accelerate transformation.