Cloud costs need active management; Palantir and Cloudflare are working together to help companies address that requirement.
Ronak Mathur shares three ways that CXOs can keep enterprise-wide AI and automation adoption moving forward.
Software composition analysis tools are valuable assets to secure systems and protect organizations, says Frank Domizio, but they will also directly benefit software developers.
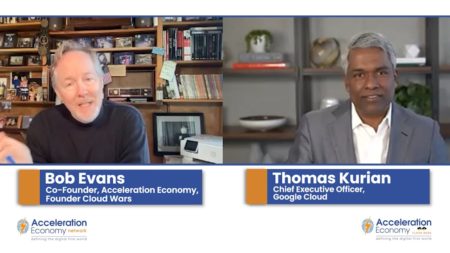
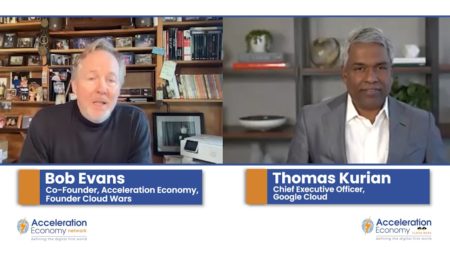
In this CEO Outlook moment, Thomas Kurian explains why he thinks edge computing, cybersecurity, and the mainstreaming of AI will have the most impact this year.
Why is sustainability critically important and how does technology play a key role? This guidebook answers that question by delivering real-world insights, actions, and guidance to achieve sustainable outcomes.
CIOs and CISOs must learn to communicate openly to have the types of strong relationships that lead to healthy, successful companies. In this analysis, Kenny Mullican gives tips on how they can achieve them.
Learning when to say no is an important skill for CISOs, particularly, Robert Wood explains, when it comes to trendy or complex technologies and partnerships.
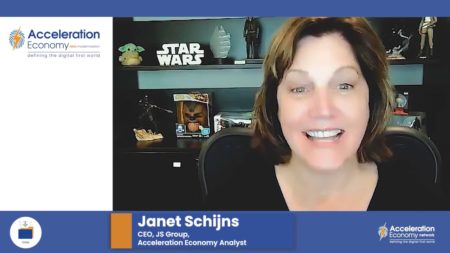
Drawing on examples from the retail and healthcare industries, Janet explains why partner strategies may be the missing link for modernizing data.
How do cybersecurity companies manage the complex nature of IT environments? In this Cybersecurity Minute, Robert Wood explains why portfolio companies have the solutions.
Automation tools can make errors, which surfaces the need for a recovery plan in case something goes wrong, says Kieron Allen.
From an openness to new technology and evolving company culture to advances in hyperautomation and generative AI tools, the Growth Swarm podcast covers the many reasons why there’s never been a better time for business modernization and transformation.
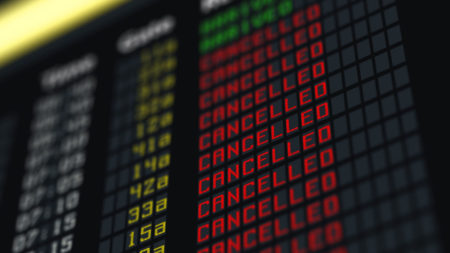
Think your company is immune to a SWA-style meltdown? Not so fast. Wayne Sadin explains why CXOs must implement technology oversight in four key areas: capacity risk, project risk, disaster risk, and technical debt.
Google Cloud CEO Thomas Kurian discusses customer buying patterns and priorities, 2023 trends, and how a customer focus attracts great employees.
Do you know how to respond after a security breach has happened? This “for CISO, by CISO” guidebook provides first-person actionable insights from practitioners.
Wayne Sadin continues his discussion on the recent Southwest Airline meltdown and how it demonstrates the perils of ignoring regular maintenance of a company’s systems.
Frank Domizio explains how a modern CISO can communicate security needs and strategies to top leaders, peers, and their cybersecurity teams.
This guidebook is your 2023 Cloud Wars Top 10 Roadmap on Microsoft, Amazon, Google Cloud, Salesforce, Oracle, SAP, ServiceNow, Workday, Snowflake, & IBM
Drawing upon his experiences in the C-suite buying and selling technology, Tony Uphoff explains the value, for leaders, of staying on top of the cutting edge.
In episode 41, Wayne Sadin uses the airline’s recent flight cancellation crisis to demonstrate the need to look at all of your IT risks, not just one of them.
In this Cloud Wars Expo Industry Cloud Battleground Moment, Carrie Tharp explains how Google Cloud emphasizes security and privacy in the hospitality industry.