Lookout today released its Global State of Mobile Phishing Report, which paints a daunting picture for organizations using mobile devices as part of their corporate computing infrastructure — that is, virtually all enterprises: the number, sophistication, and impact of phishing attacks are all rising significantly.
The data comes from over 210 million devices that Lookout protects, explained Lookout’s Chief Strategy Officer Aaron Cockerill in an interview. “Our software allows us to look at URLs that are sent to these devices for legitimacy, to establish whether there are, for example, malicious links, phishing links, that type of thing.” Lookout’s security platform protects corporate data and systems from endpoints to the cloud and the company is on Acceleration Economy’s Top 10 Shortlist of Cybersecurity Enablers.
“We’re ingesting over 4 million links a day, and we analyze those new links to see if they are potentially dangerous,” Cockerill adds.
Lookout’s research labels 2022 the year with the highest rate of mobile phishing attacks ever: over 30% of personal and enterprise users are exposed to phishing attacks every quarter. In fact, last year over 50% of personal devices were exposed to a mobile phishing attack quarterly.
According to the report, since 2021, mobile phishing rates have increased by around 10% for enterprise devices and over 20% for personal devices — and non-email-based phishing attacks are on the rise as well. Lookout identified a seven-fold increase in vishing (voice phishing), smishing (SMS phishing), and quishing (QR code phishing) in the second quarter of 2022. The last data point underscores the multi-pronged approach attackers are taking to steal data.
“We’re not trying to sensationalize this,” says Cockerill. “We’re trying to show legitimately increasing numbers over time that would explain to enterprises the need for protection.”
In terms of monetary losses, the potential annual financial impact of mobile phishing on an organization of 5,000 employees is close to $4 million, Lookout says in the report, which lays out a detailed methodology of how it arrives at that figure.
Why Attacks Are On The Rise
There are several reasons why mobile phishing attacks have increased, but the most significant is the shift from office-based to remote and hybrid work models. The threat landscape is growing at a staggering pace, and unsecured devices are increasingly entering the enterprise environment.
New working arrangements are also creating closer links between users, endpoints, and applications — corporate and personal — helping to facilitate attacks.
“Many of us have messaging platforms that are on both a mobile device and a corporate laptop, Apple’s iMessage is a good example,” says Cockerill. “The fact that a message shows up on a corporate device which the user thinks is protected by corporate security as well as a mobile device, which is personal, gives the attack credibility.”
Duping Users
The report points to a troubling trend of end users opening phishing links at increasing rates on both enterprise and personal devices. Lookout finds that 27.6% of personal users and 11.8% of enterprise or corporate users opened six or more phishing links per year in 2022. The enterprise figure nearly doubled year over year, and it was up from just 1.6% in 2020.

Cockerill noted that attackers are succeeding at making their messages look more legitimate, with well-formatted emails and texts that appear authentic and consistent with those you would receive from a known organization. The use of multiple forms of social engineering — a combination of a simultaneous call and a text message, for example — is also prompting users to react.
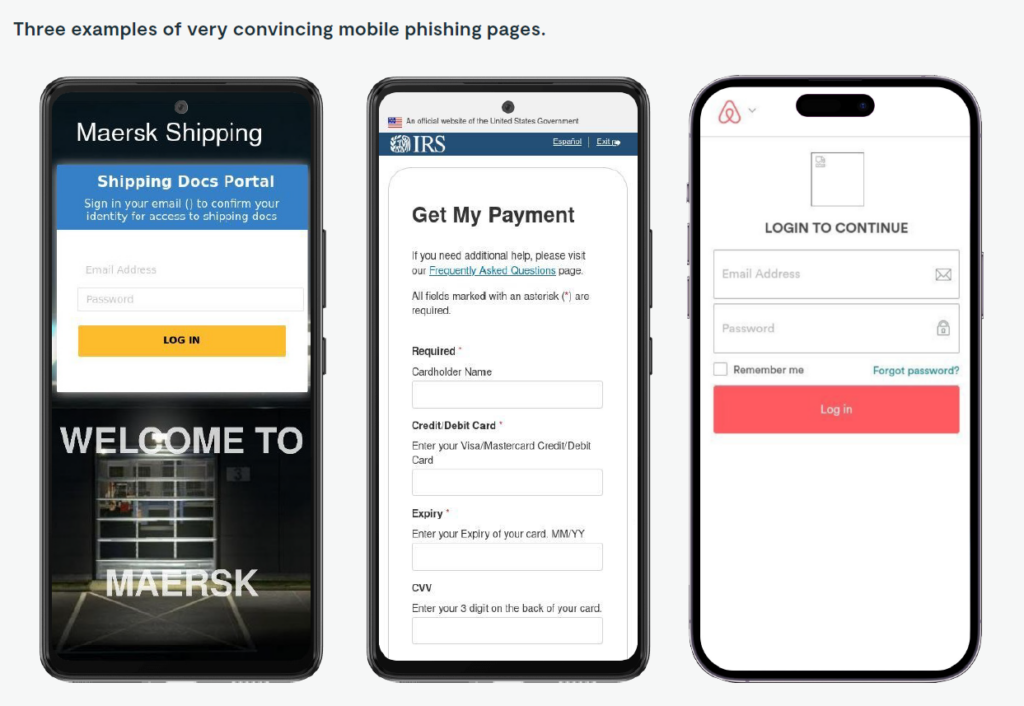
Industry Targets
Lookout’s report breaks down phishing attack targets by the industries they work in. It notes that organizations in highly regulated industries are among those most impacted by phishing attempts. In fact, those with well-documented and extensive compliance requirements and regulations have among the highest incidence of phishing attacks.
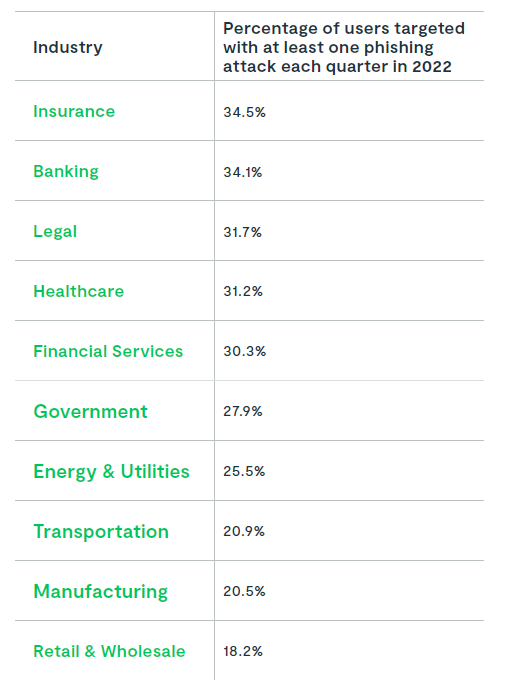
The report goes on to note that energy, utilities, transportation, and manufacturing also make the list of top attack targets and suggests these industries could be in the crosshairs because of the impact that supply chain disruptions can have on their businesses, as well as the vast amounts of logistics data and intellectual property they possess.
Cockerill noted that malicious actors are typically launching phishing attacks with the end goal of financial gain, namely stealing and selling your data. “Regulated industries possess the greatest source of that valuable data,” he says
Mitigating the Threat
With the range, and impact, of attacks increasing rapidly, I asked Cockerill for recommendations on how to ward them off. “There’s no silver bullet,” he says. “One of the most important layers of protection is filtering URLs, using a solution like our own, and that should be applied to both the mobile devices, laptops, and desktops that are operating outside of that corporate security perimeter.”

So, while filtering malicious and phishing URLs is critical, there’s more to it than that. He identified the need for ongoing training of users so they are aware of the threats and steps they can take to protect their devices, as well as your corporate data.
“Most companies these days tend to run education programs around what is a good versus a bad link, or what is a good versus bad email. All of those are increasingly important.”
“The last part of it, which I don’t see as much in training yet, is educating users about evolving tactics that are being used, like being able to identify a phishing attack where you receive a phone call that seems to be from that same company that’s sending you the link.”
Which companies are the most important vendors in cybersecurity? Click here to see the Acceleration Economy Top 10 Cybersecurity Shortlist, as selected by our expert team of practitioner analysts.












