Trend Micro is part of a new cybersecurity vendor profile series from Acceleration Economy’s Cybersecurity as a Business Enabler channel.
Who They Are
Founded in 1988, Trend Micro started with the simple idea to develop antivirus software. Little did they realize how technology would evolve – and Trend Micro adapted and evolved as well. Now, they are a world leader in security for hybrid cloud, network defense, small and enterprise businesses, and endpoints.
Led by CEO Eva Chen, Trend Micro experienced massive growth by building a culture where people “live and breathe threat intelligence”. This culture has led to collaboration with the FBI and other law enforcement agencies to stop global cyberattacks.
Further, its authority in cybersecurity is evidenced by the numbers.
employees
Fortune Global 500
businesses
endpoints protected
On top of this, Trend Micro has established strong partnerships with many of the Cloud Wars Top 10 companies such as AWS, Microsoft, Google, and IBM.

“Organizations running Trend Micro’s Cloud One on Google Cloud can benefit from a single, unified platform that brings together container, workload, network, and file storage security while leveraging Google Cloud’s global elastic infrastructure.”
Kevin Ichhpurani, Corp VP, Global Ecosystem at Google Cloud (source: https://www.trendmicro.com/en_be/partners/alliance-partners.html)
Being a leader in the cybersecurity category, and continuously fostering strategic partner alliances, means addressing things head-on. Chen gets to the core of what’s needed today:

“Vulnerabilities used to go months or even years before being exploited after their discovery. Now it can be hours, or even sooner. More executives than ever understand that they have a responsibility to be informed, but they often feel overwhelmed by how rapidly the cybersecurity landscape evolves. IT leaders need to communicate with their board in such a way that they can understand where the organization’s risk is and how they can best manage it.”
– Eva Chen, Trend Micro CEO (source)
What They Do
Trend Micro is tackling security on multiple fronts to provide customers with full end-to-end threat protection. The Trend Micro Cloud One™️ platform brings together 4 core components to provide faster, better protection.
Hybrid Cloud
Secure your physical, virtual, cloud, and container environments more effectively with the Trend Micro Cloud One™ security services platform.
Networks
Protect against known, unknown, and undisclosed vulnerabilities across IT and IOT environments with Trend Micro Network One™.
Users
Protect your endpoints, email, and more with Trend Micro Apex One™.
Extended Detection & Response
See more and respond faster with Trend Micro Vision One™, a cyber defense center that goes beyond other XDR solutions.
The goal of the platform is to address the cyber risks that face many companies. But what are the realities of these risks?

63 billion threats blocked
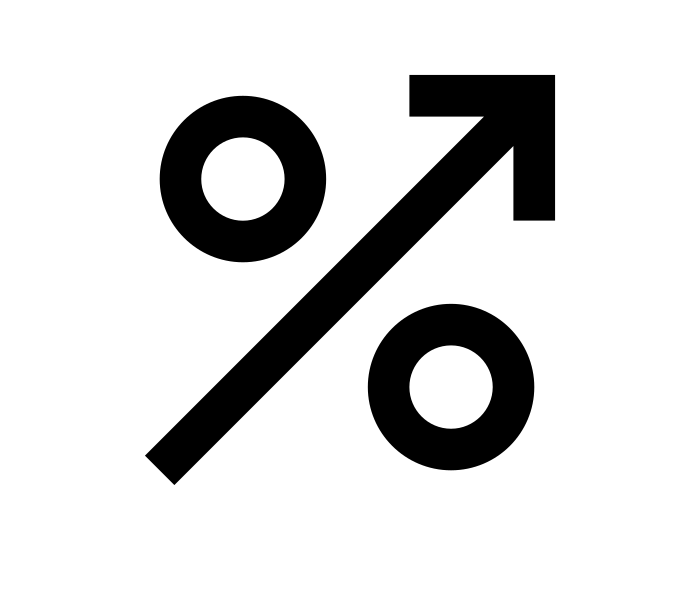
Ransomware surged by 150% year-on-year

Average cost of a breach $4.2 million+
Additionally, Trend Micro has taken the long view on cybersecurity with its Project 2030 initiative. This effort has been showcased in an episodic series in the fictional location of New San Joban and outlined in an Executive Summary and Report.
Who They Have Impacted

Since 1889, Carhartt has believed that “Our actions must always speak louder than our words, because we are worn by the hardest-working people of them all.” And, just as they equip people with clothing that needs to withstand whatever life throws at it, Carhartt realized it needed strengthen its cybersecurity posture.
The Challenge

Tim Masey, Vice President, IT Infrastructure & Security at Carhartt, noticed quickly the lack of security strategy and tools to protect its IT environment, data, and endpoints.
“I recognized that we needed to consolidate security controls and create a framework that would allow us to become a risk-adverse organization,” said Masey. “We were eager for a better solution with visibility into security events and improved manageability.”
The Result
With this in mind, Carhartt set out to improve security for the company’s 5,600 users. They implemented Trend Micro’s broad security model to achieve amazing results.
- 20 to 25 malware attacks stopped over the last six months
- 3,000 and 4,000 web reputation events blocked
- Increased endpoint protection from 50% to 98%
- 100% security visibility and improved regulatory compliance
- Reached PCI DSS compliance in 13 months
Closing Thoughts
It’s not enough to secure your internal infrastructure. Cyber-attacks can occur anywhere, and your edge and endpoint devices and locations need robust security as well.
If “end-to-end” cybersecurity is pitched to you, be sure it’s truly end-to-end. Any gaps in your security can be detrimental to you and your customers.
Data is a critical asset – protect it at all costs.
Want more cybersecurity insights? Visit the Cybersecurity channel:










