IBM’s Raj Datta shares insights on the company’s latest innovations and partnerships leading up to the IBM Think event.
Cybersecurity
Discover essential insights into recent cybersecurity vulnerabilities in Microsoft’s cloud services with this analysis of the Cyber Safety Review Board’s report.
AI-driven cybersecurity advances pose both opportunities and threats, underscoring the critical need to fortify defenses against vulnerabilities and exploitations.
It’s imperative for Microsoft CEO Satya Nadella to acknowledge and rectify the cybersecurity breach to uphold the company’s reputation and trustworthiness.
Microsoft CEO Satya Nadella fails to address a serious cybersecurity breach in China during its earnings call despite labeling security “our number one priority.”
New data clean room app — integrated into the Snowflake Data Cloud — makes cross-company, cross-cloud data sharing secure and easily accessible.
The IBM Think conference in Boston will be full of opportunities to network, gain insights on AI, cloud computing, and quantum computing, and fuel personal and professional growth.
Leveraging Google’s cybersecurity intelligence, Google Cloud emerges as a formidable player, poised to capitalize on market opportunities amid competitive challenges.
Google Cloud Next reveals CEO Kurian’s vision for advancing AI integration across its strategic clouds, driving transformative business outcomes for customers.
Microsoft faces scrutiny over a cybersecurity intrusion in China, prompting questions about how CEO Satya Nadella will address the crisis to regain customer trust.
Mastering soft skills transforms cybersecurity professionals into strategic communicators, empathetic collaborators, and compelling storytellers.
There’s been a surge in sophisticated phishing techniques, outlined in Lookout’s research, targeting cryptocurrency platforms and federal agencies like the FCC.
With a $2M commitment, Google spearheads the AI Cyber Defense Initiative, sharing the Magika AI tool, and uniting with global startups, marking a significant move towards strengthening cybersecurity resilience.
Workday’s co-founder Aneel Bhusri transitions to executive chairman, and cites six key strategic areas, including AI integration, industry-specific solutions, and cybersecurity, as the company aims to double revenue to $15 billion.
Gutsy redefines cybersecurity with process mining, a strategic tool that integrates people, processes, and technology to offer data-driven insights.
AI Index Ep 28: Super Bowl commercials highlight generative AI; Perplexity raised $73.6M; and Pecan AI develops predictive-model offerings.
Has Microsoft surpassed AWS as the leader in the enterprise cloud? Financial figures show Microsoft’s cloud revenue consistently outpacing AWS.
Analyzing the role of AI in manufacturing, this CIO guide explores efficiency gains, quality control improvements, and predictive maintenance benefits, while addressing cybersecurity, data privacy, and technology dependency risks.
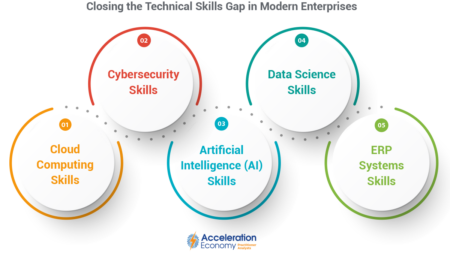
In order to prepare companies for the future of technology-driven business, it’s incumbent upon CIOs to identify and actively address the most critical tech skills gaps.
AI Index Report Ep 26: ASU embraces OpenAI’s ChatGPT Enterprise; Blueshift gains $40 million in growth investment; and Vicarius builds cybersecurity copilot.