AI, spearheaded by CrowdStrike and Google, is redefining cybersecurity, shifting it from a risk to an indispensable asset, revolutionizing defense strategies against evolving threats.
Search Results: data security (2056)
SAP intensifies focus on data with GenAI capabilities in Datasphere, refraining from “data cloud” terminology despite potential customer alignment.
Mastering soft skills transforms cybersecurity professionals into strategic communicators, empathetic collaborators, and compelling storytellers.
There’s been a surge in sophisticated phishing techniques, outlined in Lookout’s research, targeting cryptocurrency platforms and federal agencies like the FCC.
Gutsy redefines cybersecurity with process mining, a strategic tool that integrates people, processes, and technology to offer data-driven insights.
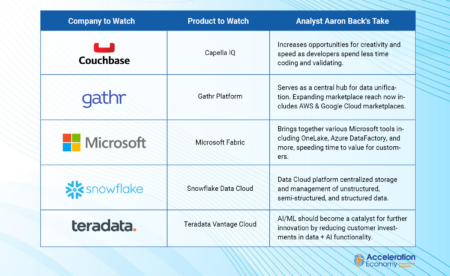
Partnering with Soracom, Couchbase makes it easier for customers to connect IoT devices in diverse geographical locations and remote areas where connectivity is often difficult.
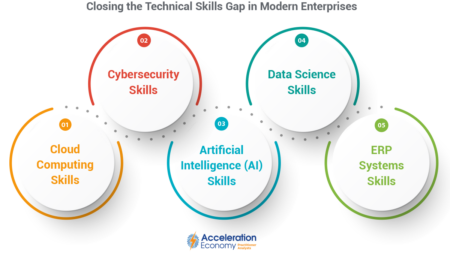
In order to prepare companies for the future of technology-driven business, it’s incumbent upon CIOs to identify and actively address the most critical tech skills gaps.
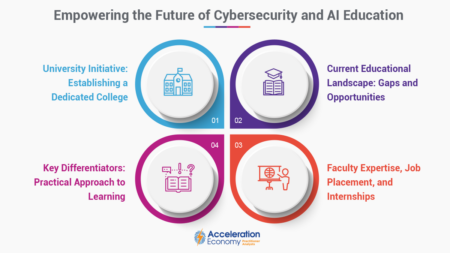
Texas university leads the charge in cybersecurity education, introducing a specialized college focused on AI and cybersecurity. Students need academic and real-world experience to succeed in these domains.
AI Index Report Ep 26: ASU embraces OpenAI’s ChatGPT Enterprise; Blueshift gains $40 million in growth investment; and Vicarius builds cybersecurity copilot.
HYCU applies generative AI to a critical enteprise use case: easily, rapidly building code that enables companies to protect data stored in their SaaS applications.
Discover our 5 data products to watch — from Couchbase, Gathr, Microsoft, Snowflake, and Teradata — and how they can support your company’s AI strategy in 2024.
In 2024, the challenges of AI adoption, cloud migration, and cultural shifts take center stage for CIOs striving to align IT with business.
AI Index Report Ep 22: Salesforce announces latest additions to its Einstein AI; Nabla secures funding for its specialized copilot; and Articul8 provides high security AI.
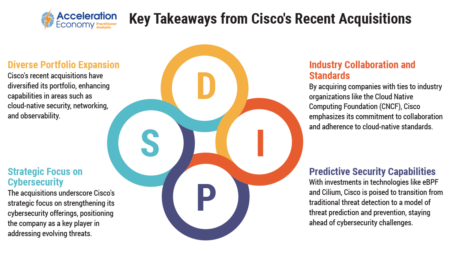
Cisco is positioning itself for the future of cloud-native cybersecurity and AI through acquisitions of Splunk and Isovalent.
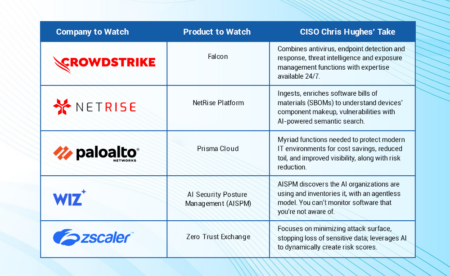
The top 5 cybersecurity products to watch in 2024 feature a healthy dose of generative AI and turnkey platforms, as well as supply chain and cloud protections.
There is significant strategic value in looking at how cybersecurity threats are evolving and how that relates to strategic business plans.
For CISOs and security leaders, grappling with the global ramifications of the EU AI Act becomes paramount, necessitating a proactive stance.
Frank Domizio explores how IT leaders can ensure their organizations are protected from security threats in a way that also enables business growth.
Andi Gutmans, VP and GM for databases at Google, highlights a surge in customer interest in modernizing their database estates by transitioning from legacy to open-source databases, driven by flexibility and cost benefits.
Wiz’s AI Security Posture Management (AI-SPM) addresses security and privacy concerns wrought by AI with comprehensive oversight, inventory management, and misconfiguration checks.