SharePoint Security Sync integrates Dynamics 365 CRM with SharePoint to provide seamless document management and security for data stored in SharePoint.
Search Results: data security (2058)
As ransomware attacks increase in frequency and complexity, businesses need to be on the lookout. Often, data breaches are due to basic and avoidable cybersecurity gaps. Learn how to address existing cybersecurity concerns and respond quicker and more thoroughly against these evolving threats.
SharePoint Security Sync integrates Dynamics 365 CRM & PowerApps with SharePoint to provide seamless document management and security for confidential documents stored in SharePoint. By syncing Dynamics 365 CRM security privileges with SharePoint, it helps to maintain data confidentiality and eliminate security risk while storing documents in SharePoint. It further enhances user experience in document management by providing various functions such as drag & drop, upload, download, generate link, email, and much more within Dynamics 365 CRM & PowerApps.
This BizTech article by Doug Bonderud addresses multiple areas of cloud encryption that you need to be cognizant of in your cloud strategy. Some take cloud security for granted based on assumptions, but making sure your data is secure from end to end is vital.
January 2021 saw some major cloud database developments in a fast-moving, fast-growing, customer-demand-driven market.
Oracle’s answer to the specialty database trend is Oracle Database 21c, a “converged database” that will take on AWS, Microsoft, Snowflake.
Some companies have allowed a large number of workers to work remotely in the past, others have not until the Coronavirus arrived. Security and access to data, like the rest of your business processes in these challenging times, needs to now be looked at a bit differently. In this webinar, we will review the steps you and your company can put in place to ensure application and user security is not compromised with a remote work force. The good news is that more than likely your company probably has many techniques in place already, or in place and ready to easily implement. However, there are some controls that are often overlooked, and a since ‘a chain is only as strong as its weakest link,’ it is critical all security controls are addressed accordingly. We will highlight these commonly overlooked controls as well in this webinar.
Accounts payable can be unorganized, unstable and unsafe, but it doesn’t have to be. With Bottomline’s Paymode-X AP automation solutions, organizations can maximize efficiency, visibility, and security by automating the entire invoice-to-pay process.
Learn how we can help your AP department:
* Standardize and accelerate invoice processing
* Centralize, automate and streamline payments
* Secure AP processes and reduce fraud
Find out more.
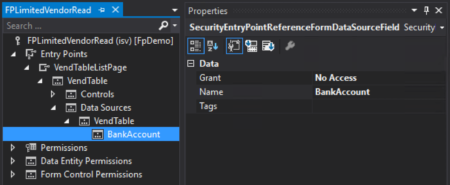
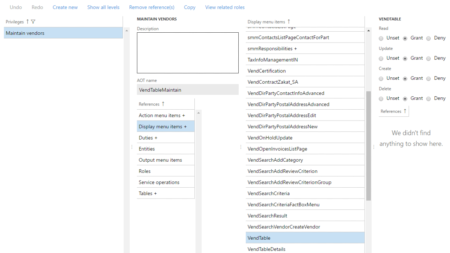
Learn how to set up field level security in D365FO.
In other posts, I talk about the effect of where you create D365FO security (AOT vs user interface) has on…
A lot!
From software corruption and system failure to natural disasters and ransomware attacks, ensuring your data and business applications are accessible and uncompromised is vital to your continued operation. Eliminate the risk and cost of IT downtime with the EverSafe all-in-one cloud backup, disaster recovery, and business continuity solution.
Data scientists and IT are often at odds with each other. However, that doesn’t always have to be the case. With key plans in place and a strategic set of goals and KPIs, these teams can work in better harmony.
The cloud database market is being upended by a new breed of providers, led by Snowflake but there are many others.
Looking at ways to improve cloud security remains a top priority for businesses. IBM Security recently announced a plan to use Amazon Web Services (AWS) to enhance cloud infrastructure security for hybrid environments.
Oracle claims that its Autonomous Data Warehouse has three significant advantages over category-king Amazon and shiny new object Snowflake.
If you manage the security of your company’s data, while challenging, you also have the opportunity to be a champion for your company with the right tools. In this session, learn how Fastpath can help provide your company to answers important questions like: Do you know who has access to your data, what they are doing with that data, and the risks to your data? With the Fastpath Assure cloud platform, you can answer these questions and provide an internal control framework to meet your compliance needs. Get rid of manual, prone to error, security related tasks and replace them with solid controls around user access, segregation of duties, tracking changes to critical data, and setting up new users. Fastpath will help your company take your security by design to the next level. We also will review the native controls in Dynamics 365F&O/AX around security, showing where Fastpath can help fill gaps and improve efficiencies in security reporting. In today’s world, with GDPR, SOX, and ever-growing number of audits, having the right security and financial controls in place is more important than ever. This session will show how the Fastpath governance, risk, and compliance solutions can help your company become a security and compliance superstar.
Dynamics 365/CDS security is not applied automatically in Power BI. This session will cover all the pitfalls of the security model so you know how to avoid them and ensure people only see the right records. Either if you are connecting directly to CDS, or use either the Data Export Service or Data Lake. There’s additional flexibility in this setup where we can tailor what data we show users. Session includes a demo of the methodologies, the POA table, and how some security roles can be exported to Power BI and used to apply similar security requirements in the reports.
The content of this session is geared toward an audience with advanced-level knowledge of the subject area.
Some companies allowed remote workers in the past, yet others have not until the Coronavirus arrived. Security and access to data, like the rest of your business processes, needs to now be looked at a bit differently. The good news is that it’s likely your company has many techniques in place already, or ready to implement. However, some controls are often overlooked, and a since ‘a chain is only as strong as its weakest link,’ it’s critical all security controls are addressed. Discover commonly overlooked controls and the steps to ensure security is not compromised with a remote work force.
The content of this session is geared toward an audience with beginner to intermediate-level knowledge of the subject area.
This session will be available for CPE credits pending completion of session survey post event.
In the launch of new cloud services last week, founder Larry Ellison clearly made “autonomous” the third strategic front in Oracle’s plan to beat Amazon.