There are a lot of questions about security in D365FO and how it differs from previous versions of AX. If we look specifically at user permissions we can see a couple of things that have changed.
In AX the access level is hierarchy based with one access level being assigned to each object:
No Access -> Read -> Update -> Create -> Correct -> Delete (Full Control)
An excerpt from an MSDN on the topic has the following:
“Read is the weakest permission, and Delete is the strongest. Delete permission includes every other permission. Create permission includes Update and Read. You can set the permission value to NoAccess to prevent all access to the entry point.
The Correct permission applies only when a time state table is involved. This permission authorizes you to issue update records in a time state table.”
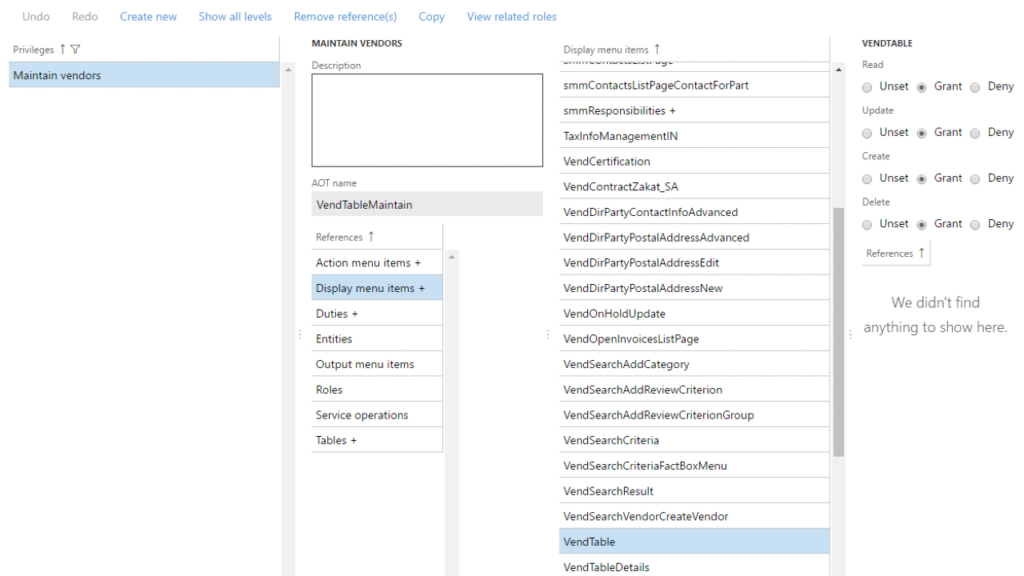
Below you can see that you are only able to assign one Access Level per object.
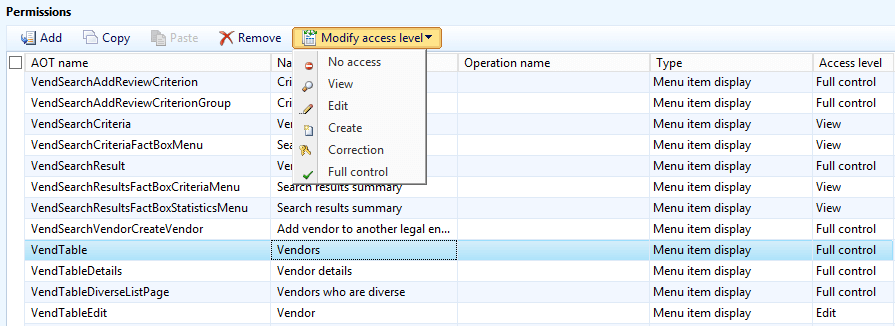
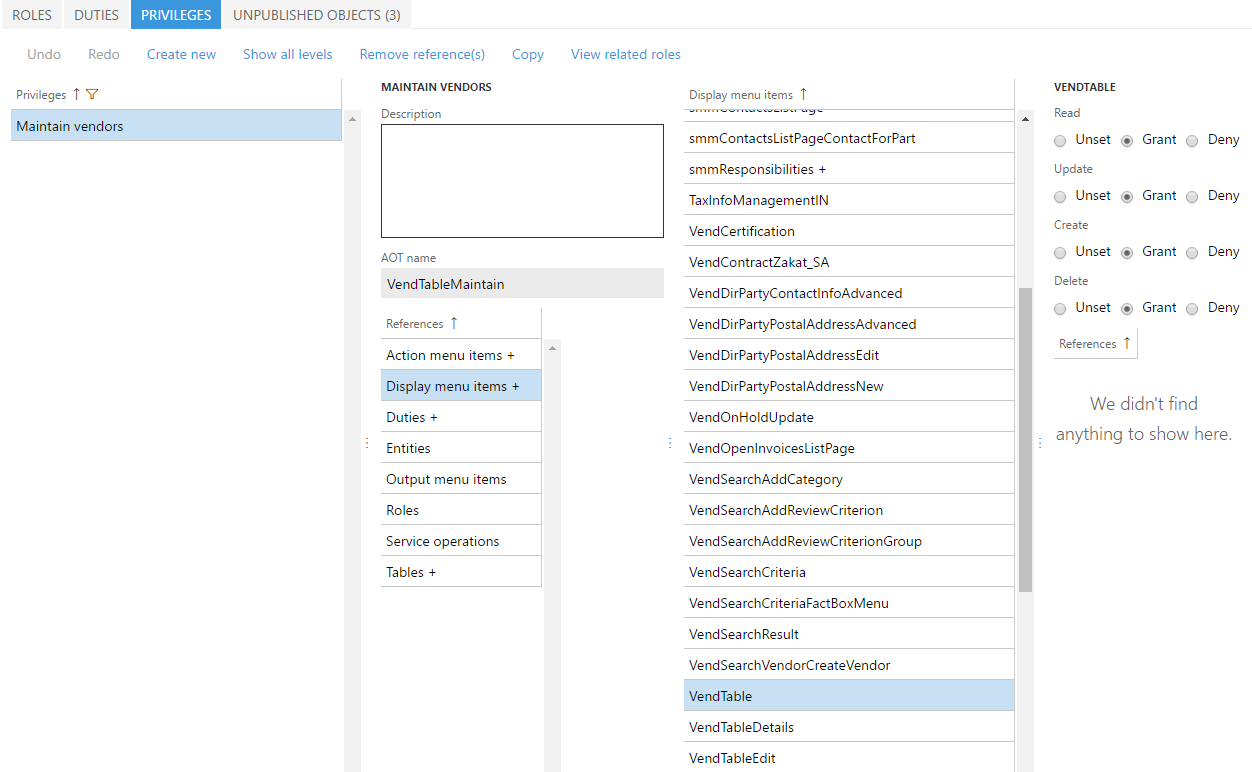
In D365FO the permissions still follow this hierarchy of permission strength but allow for a piecemeal assignment. This means you can individually select Read, Update, Create, or Delete for each object you are securing. There are also different access types for each access level: Unset, Grant, and Deny. Grant means that the user has the ability to this access level for this object, and Deny means that the user is explicitly being denied this access, and Unset means you are not granting nor denying access to the object so if another role, duty, or privilege grants access to the object then the user will have access.
One thing to keep in mind, is that the Deny access type overrides any Grants assigned to the user for this object from any role, duty, or privilege.
D365FO also has a new data type called a Data Entity. A data entity is basically a SQL view that will take a normalized database object that could exist across multiple SQL tables and creates one object that an end user can interact with. It is a very powerful feature that can be used by developers and 3rd party applications to interface with D365FO.
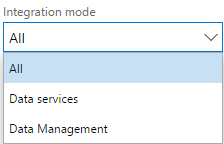
Permissions for a data entity include one more property called Integration Mode. This setting will dictate if this element is accessible from OData and/or an import/export or connector integration.
Entry pointDescriptionData servicesThe ability to use OData services (API) for the entity.Data managementThe ability to use asynchronous integration options for the entity, such as import/export and connector integration.
These changes in the security model will need to be kept in mind when designing and applying security to an end user.
You can find more posts like this on my blog at: http://d365foblog.com