In a previous article, we discussed confronting cybersecurity with data, particularly quantifiable metrics. The cybersecurity industry traditionally has measured and conveyed cyber risk in subjective qualitative terms and concepts. This has led to a disconnect from its business leadership peers, especially as cybersecurity continues to get escalated to the boardroom with emerging changes from the Securities and Exchange Commission (SEC), as well as broad concerns for cyber risks. In this article, we discuss a popular quantitative risk management framework that addresses the concern.
Introducing FAIR
The framework is the Factory Analysis of Information Risk (FAIR) model for cybersecurity and operational risk. FAIR is led by the FAIR Institute, which boasts more than 13,000 worldwide members, 45% of Fortune 1000 organizations, and 23 local chapters. FAIR’s overarching goal is to shift from a compliance-centric approach to a risk-based approach for cyber risk quantification.
FAIR recognizes that in today’s digitally driven society, organizations use technology and software to empower business value delivery. All of those systems and software are subject to cybersecurity risks. That risk is business risk, which must be communicated in business terms and figures, something the cybersecurity industry has traditionally been poor at, despite calls to “speak the language of the business.”
FAIR argues organizations already manage risk, but most are doing it implicitly and should be doing it explicitly. This means shifting to a quantified risk target that the organization measures and manages against. This also requires the organization to have established a coherent risk appetite framework.
A Deeper Dive Into FAIR
FAIR aims to have organizations utilize quantitative risk models that leverage people, processes, and technology to empower organizations to achieve acceptable levels of loss exposures. This means that rather than traditional subjective measures of cyber risk management, organizations have accurate models with meaningful measurements and baseline data to drive well-informed decisions.
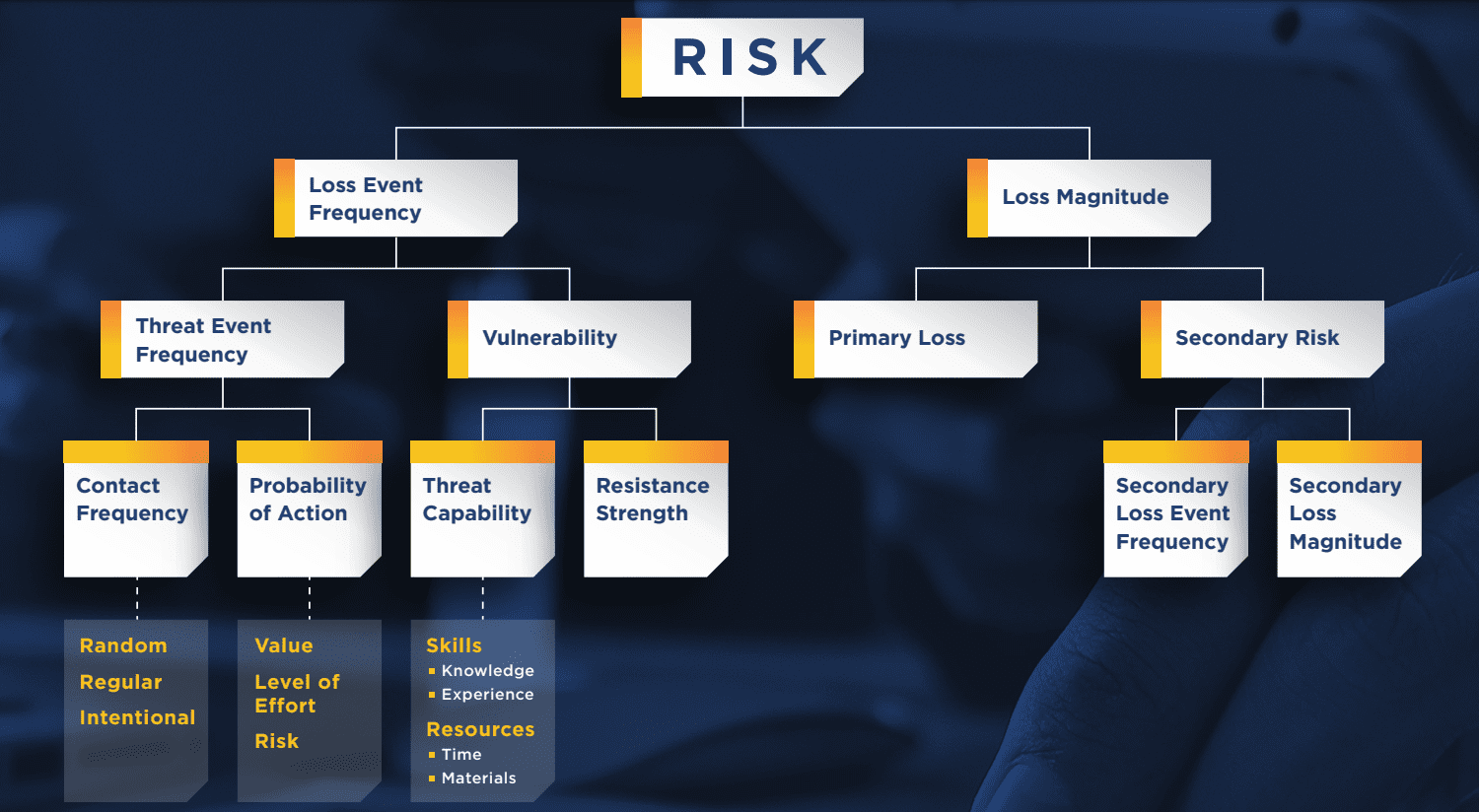
As evident from the above FAIR Flowchart, measuring cybersecurity and operational risk requires a more mature approach, including defining fundamental concepts and metrics that most enterprises simply haven’t done. These include metrics such as loss event frequency and loss magnitude as well as subsequent metrics such as primary loss and secondary risk.
Measuring cybersecurity and operational risk also requires organizations to do fundamental activities such as identifying all their assets and relevant threats as well as understanding the various potential loss events and their associated potential impacts accurately. On the surface, this sounds simple, but organizations have struggled for decades to accurately inventory their hardware and software assets. The issue is only getting worse with the advent of the cloud, where shadow information technology (IT) can proliferate with a few clicks and corporate credit cards.
That said, all is not lost. There are several resources available for individuals and organizations looking to get serious about cyber risk quantification via the FAIR model. There, of course, is the book “Measuring and Managing Information Risk: A FAIR Approach” and even FAIR training and certifications.
Final Thoughts
You may be questioning why all of this matters. The reality is that if we, as a cybersecurity industry, want to be taken seriously by our business peers, it requires speaking their language and this means tying cyber risk to the business, and not in a subjective speculative manner, but through metrics and quantifiable data around assets, risk, and loss. It is hard to advocate for an increased budget for the cyber program or investments in insurance, staff, training, or any related resources if we can’t articulate the current state of the organization’s assets and data as well as the risk associated with them.
As an industry, cybersecurity long has bemoaned being neglected at the proverbial “seat at the table” and the desire to be escalated in the conversation. That escalation requires a maturing not only on the businesses’ part but also among cyber practitioners.
Want more cybersecurity insights? Visit the Cybersecurity channel: